I've written 2 reviews for VPN Services recently:
I've also written 2 reviews for WIFI VPN/TOR portable boxes:
One item I have never covered is the proliferation of scammy VPN services sold by snake oil salesmen.
With the Edward Snowden leaks and all the media coverage about the loss of online privacy, even the most complacent internet netizens are starting to think about securing their online presence. Protecting it not only from government agencies but from unscrupulous websites and even their own ISP (Your ISP is watching you).
So what was once the domain of geeks and corporations (VPN) has now become mainstream. The truth is the tech behind VPN is complicated for the average Joe to understand and most are simply not interested in digging into the details. It is this nonchalance that attracts scammers trying to make a quick buck.
Example of scam VPN Service
MySafeVPN was a fake VPN service created by unknown bad guys trying to scam users. They obtained a confidential Plex database and used the customer emails as targets. Each target received an invitation pretending to come from Plex and offering their brand new VPN service called MySafeVPN (discussion thread here).
Once Plex found out about this fake service, it provided an official rebuttal statement to its users. The scammers quickly disappeared and took the money raised with them.
Copying legitimate services
“Imitation is the sincerest form of flattery that mediocrity can pay to greatness.”
Scammers are inherently lazy and love copying what already works. They often copy the look, feel and content of legitimate VPN providers, making it hard for the "average Joe" to distinguish the good from the bad.
Telltale signs of a scammy VPN provider
It's free or unreasonably cheap
Running a VPN service costs money. Providers have to pay for hosting, servers, development and connectivity. If the price is unreasonably cheap, it may just be a pretty interface to public proxy servers or they probably have another revenue stream (like selling your services or injecting malware into your traffic).
Reputation, reputation, reputation
Search the web and figure out how long the service has been in business. Unless I know something about the founders, I tend not to trust new VPN services (e.g. ProtonMail create ProtonVPN so I trust them). Search forums for comments (positive or negative). If a bunch of the comments seem to be posted around the same time period, assume that they may be fake.
Outrageous claims
Reputable services provide a certain level of technical detail to backup all of the claims they make. As an example, ProtonVPN has a "Secure Core" technical which enhances security and privacy. In addition to just talking about it, they provide the technical details about how it works. Beware of VPN providers that make grandious claims without any technical supporting information (e.g. The fastest, the most secure, etc).
Support model
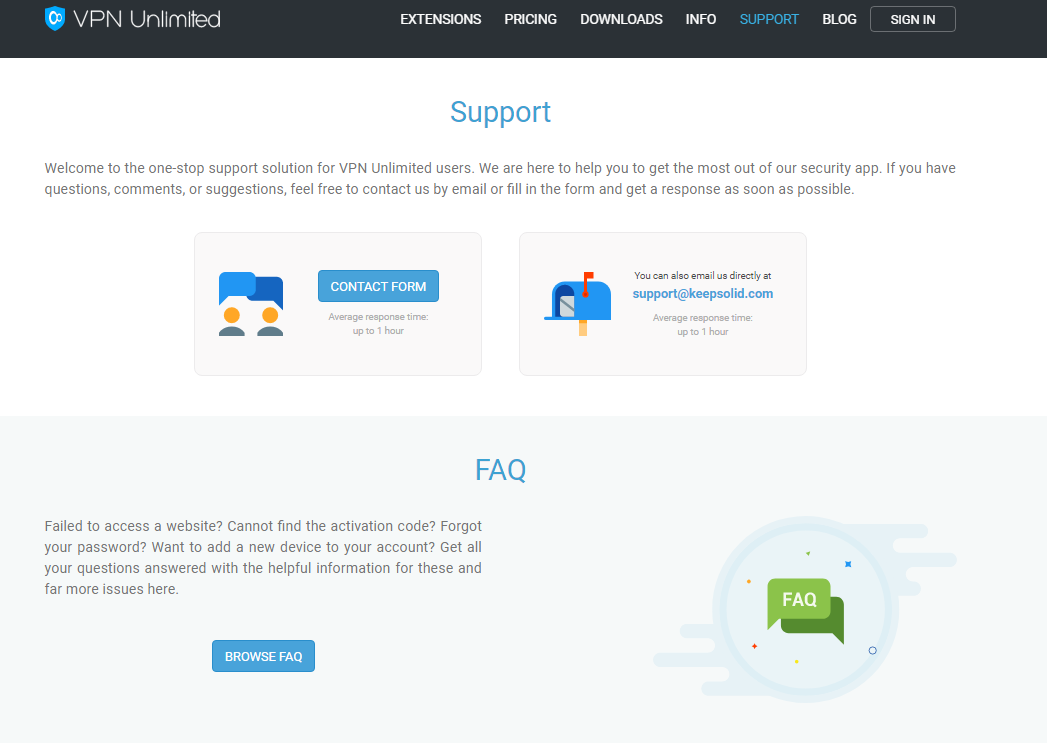
A real VPN provider will have solid support channels to ensure it's customers are happy. As an example, KeepSolid VPN Unlimited provides support via online form and email. Additionally, you can contact them via Twitter. When you submit a question, they will respond within a reasonable timeframe (even if you are testing the service or aren't even a customer yet).
Conclusion
Like all fraud, detecting fake VPN service isn't always easy or straightforward. I hope the tips and tricks I have provided here will help some of you avoid these unscrupulous scam artists. As always, if you have questions or comments, feel free to post a message below or tweet me (@ekiledjian). I normally answer questions within 48 hours.