As a frequent traveller, I have picked up some tricks that make travelling a lot easier. I wanted to share some of those with you and hopefully make your life a little easier.
Global WIFI Hotspot
I wrote my first review of the (gen 1) Skyroam Global hotspot in 2015 and it became one of my most used travel items. When they released (gen 2) a new LTE capable model, the Skyroam Solis, I bought one and reviewed it as well.
TL;DR: I have tested dozens of global roaming services (hotspots and global SIMs) and the product I carry in my bag every day is the Skyroam Solis.
Some readers have asked if my Skyroam tests were promotional and the answer is no. I have not received any compensation from Skyroam to test and review any of their products. When I find something that works well and is priced competitively, I recommend it.
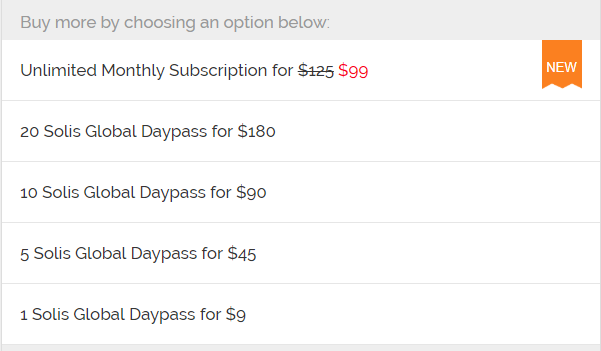
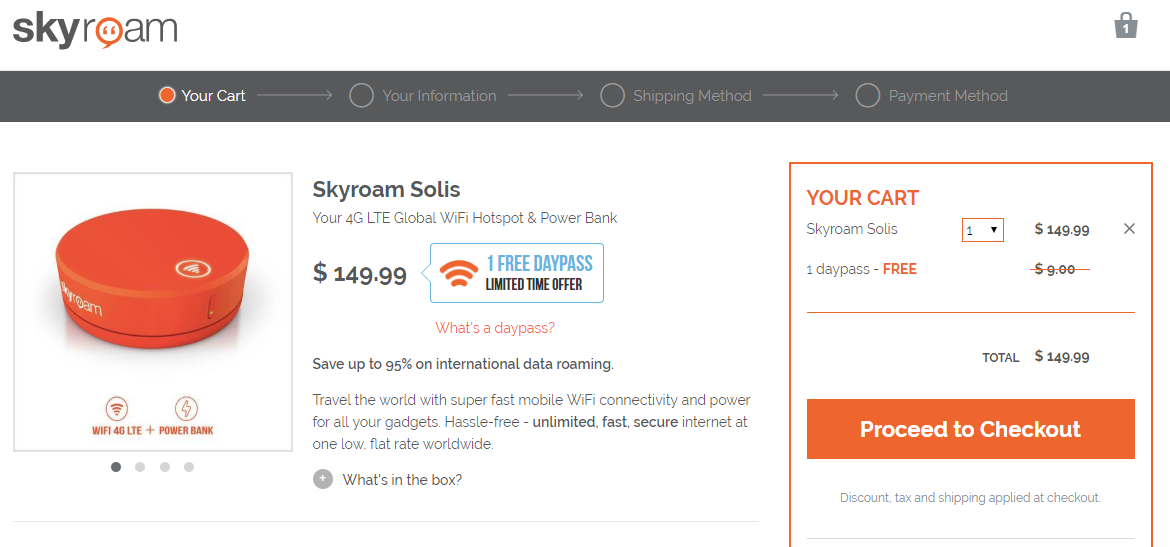
I recommend you read my full review, but the summary is that the Skyroam Solis is a pre-paid global 4G (LTE) capable hotspot that works in 100+ countries. They offer an "unlimited" data package sold in chunks of 24 hours (day passes) for about $9 a day (or a monthly pass for $99).
Most companies offering this type of service label their offering as "unlimited data" but this doesn't mean you can stream Netflix while cruising the french riviera. Every company I have reviewed imposes some type of "fair use policy". Skyroam's Solis day pass never cut-off your data access but does slow it down to a painful (and barely usable) 2G after you consumer about 500MB per 24-hour period. This period resets during each day pass. This means that you shouldn't be streaming music or videos (Spotify, Google Music, Apple Music, Youtube, Netflix, HULU, Amazon Video, etc).
As an example, the GeefiGlobal WIFI hotspot fair use policy says "GeeFi will begin limiting the download speed after you exceed 500 MB (megabytes) of data in most countries".
Frequent travellers can buy a Skyroam Solis WIFI hotspot for $149.99 (includes one day pass worth $9). Infrequent travellers can rent a Skyroam Solis with the appropriate number of day passes for $9.95 a day (basically $1 per day to rent the unit plus shipping costs back and forth).
Collapsible water bottle
I wrote about the Nomander collapsible water bottle in 2016 and still recommend it for travel.
TL;DR: The Nomander water bottle is a light flexible easy to pack piece of kit you can store easily and use when needed. It avoids having to pay $5 for a 500ml bottle of water that would otherwise cost $0.50 anywhere in the "real world".
The Nomanderis made from food grade silicone so it doesn't retain smell. It is leakproof. Where my older recommendation (the Vapur) becomes giggly when less than 3/4 full, the Nomander retains its shape fairly well for a foldable bottle.
With the plastic sleeve in the middle, the bottle is sturdy enough to stand on its own. The Nomander is (top rack) dishwasher safe, You can also freshen it up, like most other water bottles by soaking a mixture of filtered water and fresh cut lemons for 24-hours.
The water filter
Browse the aisles of any camping goods store and prepare to be amazed at the dozens of water filters available for your immediate purchase. I have been camping most of my life and have travelled to many locations known for terrible horribly diseased water.
I have tried over a hundred filters, tablets and sterilizers. The one I keep coming back to over and over is the Grayl. I first wrote about the Grayl water filter in 2016 and have been recommending it since. It beats every other filter I had tried before or that I have tested since.
TL;DR: The Grayl water filter is the easy to use, easy to carry, low maintenance and high-reliability water filter you want when in the backcountry or when travelling to locations with questionable water sanitation practices.
When using the orange travel filter, you purify and sanitize the water with one (strong) push. This means I no longer carry a UV sterilizer (Steripen) in addition to a filter (Lifestraw or Sawyer mini).
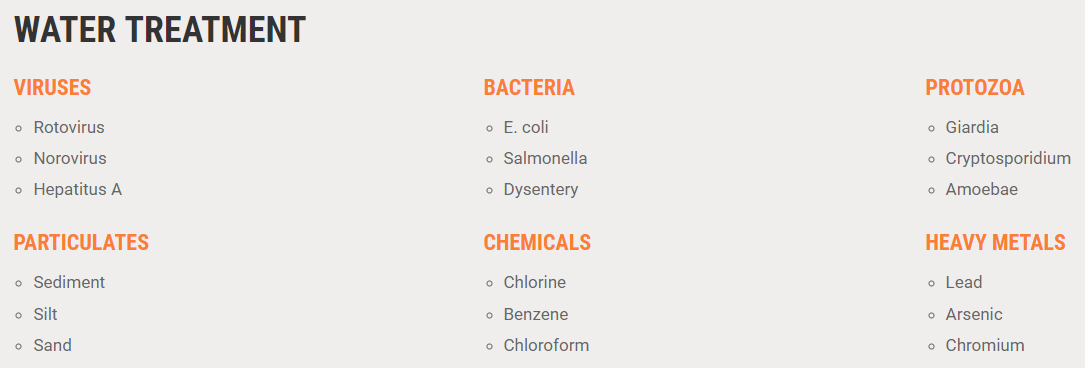
The Grayl Orange Travel filter removes:
Each cartridge lasts about 300 uses (with 3 full uses a day, a single filter would last 100 days). The filtering process requires a bit of brute strengh but you never have to worry about batteries and there is no need to backwash the filter.
Portable laundry machine
Everyone starts travelling with lots of extra clothes and big check-in pieces of luggage. Eventually, you learn that one-bag travel is the only way to go. One-bag travel does mean you are travelling with the minimum and thus may need a way to clean your clothes while on the move. 5 years ago I bought a Scrubba wash bag and have brought it with me on almost every trip (longer than a week).
TL;DR: The Srubba is a waterproof bag with scrubbing "teeth" you can use to clean your clothes anywhere in about 10 minutes.
Scrubba has become a trusted travel item for business trips and family adventures (vacations with kids, camping, road trips, etc). I use this with either Woolite Travel Laundry Soap individually packaged travel packets or Dr. Bronner organic Castille soap. Both of these detergents are gentle, work with all types of materials and wash out easily without leaving a soapie residue.
Airborne and NoJetlag
I started taking both of these products 6-7 years ago and believe they help keep me healthy when travelling (particularly the long North America to Asia flights).
I am not a doctor and the effect could be nothing more than placebo but since I started taking Airborne on longer flights, I find I get sick a lot less Worst case scenario, it is a vitamin C supplement but my experience has been very positive. I have managed to stay healthy even with colleagues have gotten sick.
When travelling to faraway destinations, I started using No-Jet-Lag. While consulting for Cathay Pacific Airlines (based in Hong Kong), a flight attendant recommended it and I have used it ever since (when travelling through more than 4-5 time zones).
The simple rule of thumb is to chew on one tablet, every time your plane takes off and every time it lands. Then chew on one tablet every 2 hours while in flight. I normally follow the manufacturer instructions and take it an hour before or 2 hours after a meal.
I'm the first person to admit the questionable medical value of homeopathic products and my results may be nothing more than a placebo effect but it has worked for me and has been recommended to me by about a dozen different flight crew members.
Tom Bihn Synapse 25 backpack
Talking about backpacks is almost akin to talking about religion. It seems people are easily offended when you recommend something different than their preferred bag. Unlike the average traveller, I have 1M+ miles under my belt and have recently tested about 25 different (well rated) backpacks before I recommended the Tom Bihn Synapse 25 backpack February 2018.
TL;DR: If you can only buy one backpack (EDC, work and travel), I recommend the USA designed and manufactured Tom Bihn Synapse 25 backpack.
I recommend you read my full review here. This bag is light, durable and has carefully designed features that will make travel much easier. Plus it is built like a tank and will not break on your mid-trip.
Best carry on luggage
I first recommended the RedOxx AirBoss in March 2012 and it has been my favourite carry-on luggage since. I have tried 50-60 different products since and always come back to this thing. It is designed to last and comes with a no questions lifetime warranty. Along with Tom Bihn, RedOxx offers the best warranty in the business.
The RedOxx AirBoss is a 100% USA designed and manufactured bag. It is made from incredibly resilient materials. The bag you see above has travelled 1,000,000 + miles since 2012 and it looks almost brand new.
- Since does not have wheels, I am rarely asked to check its size.
- It has a flexible shell which means I can push and shove it into even the smallest overhead compartments.
- It doesn't waste any room on wheels and a pull handle which maximizes available space
- It can be used with or without packing cubes
If you could buy only 1 luggage that will have to last 10+years, this is the one.
Pacsafe anti-theft packs
There are times when you will be travelling to riskier destinations where theft is a real constant concern (Shanghai, Delhi, Mumbai, Barcelona, etc). Then travelling to these "special" locations, you may have to take specialized gear to stay safe and no one offers a wider selection of anti-theft backpacks, packs and bags than Pacsafe.
I own both a Pacsafe backpack and a shoulder pack. Both of my products are no longer offered but you can easily find something that would meet your needs. During "normal" trips, I would choose the lighter and more functional Tom Bihn Synapse 25 every time but when I need extra security, the Pacsafe products are a must. The bags are lined with a metal mesh to prevent theft by slashing. Even the shoulder straps are reinforced with metal mesh to prevent a slash and go incident. Best of all, the Pacsafe bags look like normal everyday products.
I own an older version of the Metrosafe and found an everyday use for it you may find interesting. In addition to keeping my valuables safe while I travel, I use it when at the beach or public pool. I lock it to a bench or medium tall tree and know my valuables (glasses, wallet, cell phone, etc) will be there when I get back. When at the beach, I can go swimming without worrying that someone will steal my wallet. All you have to do it pair it with a travel cable based lock.