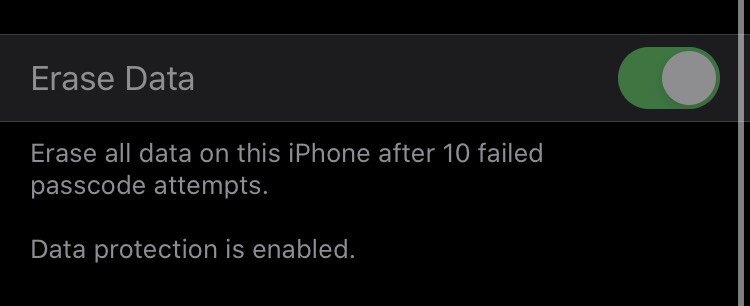
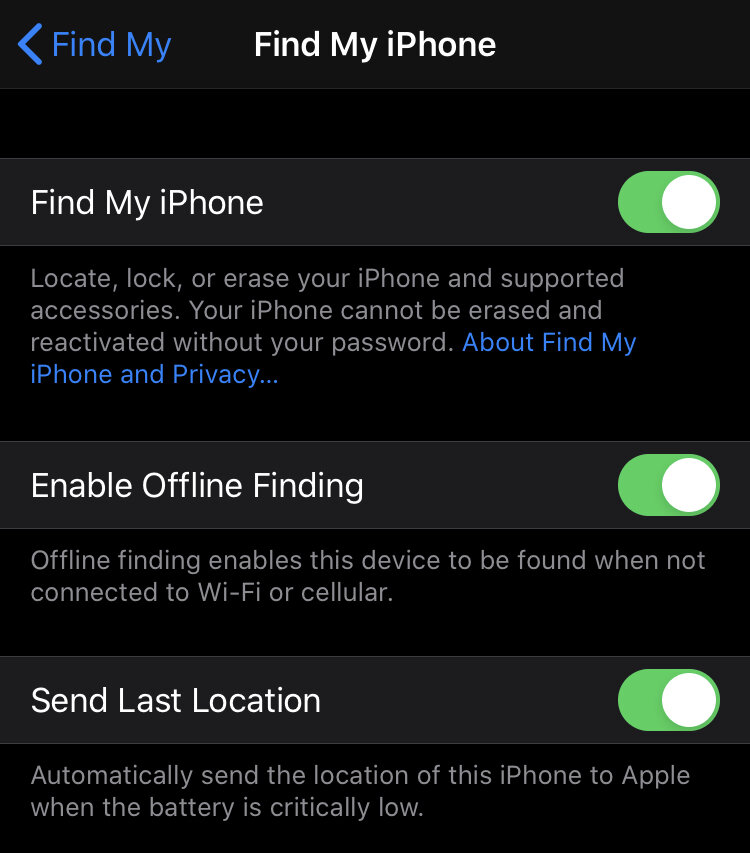
Find my device links
Two Factor Authentication
Remember that your phone is an extension to your online Google or Apple ID. It is very important that you protect these from unauthorized access. You should be using a long, complex, non-dictionary, passphrase to log in. You should also enable two-factor authentication to add another layer of protection to your account in case your password is compromised.
The easiest is to use Time based One Time Authentication codes.
On Apple devices, you will use your smartphone (or any other Apple device connected to your account. The Apple instructions are here.
Google users can use a software TOTP system with any one of the free TOPT clients available. The cleints I recommend are :
or some password managers (e.g. 1Password) also offer this as a function. The most secure option is to use a hardware token (e.g. Yubikey) but this is slightly more demanding and I won’t be covering it here.
Update and uninstall
Most attacks are against old vulnerabilities that remain unpatched. If you have a phone from a manufacturer that does not regularly deliver (monthly) security updates or the updates for your phone have stopped then it is time to buy something else.
You must update your phone operating system and all the apps on it regularly. Doing this will reduce your attack surface (ake make an attackers life more difficult).
Remember that applications may have undiscovered or unpublished vulnerabilities. In addition to updating them using the Apple AppStore or Google Play, you should uninstall any applications you do not regularly use. Many of these apps are stying on your anyway but they could be the weak gateway an attacker gains access to your phone.
Where possible, use the web version of services. As an example, instead of using a Twitter app (on most of my devices), I use the PWA website at mobile.twitter.com. This gives me full functionality without needing an app (that can track me or compromise by device).
Only install apps from official apps stores (Apple AppStore or Google Play). Apps in these stores are cryptographically signed to prevent impersonation by attackers. If you are a little more adventurous (on Android), you can also check out the F-Droid alternative app store.
Reboot often
We have seen many attacks in the last 3 years that are not persistent. This means they go away after you reboot your device. This is why it is a good idea to regularly reboot your device. I typically try to reboot it every 8 hours or so (while I am awake).
Turn off your phone
A phone that is off can’t be attacked.
An unsophisticated attacker will not be able to compromise your phone’s baseband chip and turn on your phone.
It is a good idea to turn off your phone when you can (at night or when you will be away from it from a while). Plus turning it off while charging will often allow your phone to charge a bit faster.
Install a firewall
You may not know it but if you use a Windows or macOS device, there is a manufacturer-provided firewall on your device. Unfortunately, smartphones do not come bundled with them but they are extremely useful.
It seems every week we read about another couple hundred apps (on IOS and Android) that made it to the app store but that were malicious. A firewall will define what apps will be permitted to use WIFI and/or LTE.
The best firewall for Android is Netguard and the best one for IOS is called Lockdown.
These apps can work in 2 modes:
blacklists mode, is where you choose what apps should not be allowed to communicate
whitelist mode, is where no apps can communicate unless you specifically allow them to
Obviously whitelist mode is the most secure but may require a little bit of tweaking when an app just doesn’t work right.
Due to recent societal changes, expect the authors of these apps to change the above terms shortly. Blacklist will be changed to blocklist and whitelist will be changed to allow list.
Disable WIFI and Bluetooth
Anytime you are out of a trusted location (home or work), turn off WIFI and Bluetooth. Also make sure that any feature that would automatically turn them back on is disabled (e.g. Automatically connect to public networks).
Attackers can set up a malicious network and easily trick your device into connecting to it. This is trivial but not part of this discussion so I won’t explain how to do it here.
Many public venues (e.g. malls use your phones Bluetooth beaconing to track you as you walk around. This works without any intervention from you. When you don’t need Bluetooth, turn it off.
Remember that public WIFI is evil. Any WIFI that you don’t control can be used to steal your information. If you have to connect to untrusted WIFI, use a VPN. Please use a good VPN and know that good VPNs are never free or extremely cheap. You get what you pay for.
Many will recommend TOR but it is slow and most users would find the experience painful. So I stopped recommending TOR for most users.
Browsers
Browsers are dangerous. Dangerous. Dangerous. They run code delivered to your device from another computer which means it could be a wonderful way for someone to compromise your device remotely.
If you don’t believe me, read this article China hacked iPhones and Android devices to target Uyghur Muslims.
For iPhone users, I recommend sticking with the built-in Safari. Apple has done a relatively good job with it and it should be secure enough.
On Android, my browser of choice is Bromite . Bromite has native support for the uBlockOrigin adblock engine( the best in my opinion). It supports DNS over HTTPS, to encrypt your DNS queries. It is always in incognito mode and it offers many more wonderful security-friendly features. Remember to turn on HTTPS everywhere in it and disable Javascript.
Is IOS more secure than Android?
To close out this article, I will quickly touch on the question I receive the most often.
For this discussion, we have to separate privacy and security. This article was written to improve your security not your privacy. They do not usually go hand in hand.
For a general user looking for a no worry relatively secure platform then IOS is probably the way to go.
For a general user that doesn’t mind a little work and that wants good security, Android is the way to go. IT offers more customization options to make your device more secure.
For a more security-conscious geek, then I recommend going to GrapheneOS. GrapheneOS will require some work (you have to install it) and will make you uncomfortable (does not come with any Google services or the Google Play store) but it is the most secure consumer option right now.