TL;DR: If you are using a Chromebook that is actively supported, you are probably fine.
Specter and Meltdown are two significant chip level vulnerabilities that kicked off the 2018 security scene with a bang. Affection millions of devices from almost every manufacturer, many consumers are panicking about what this means for them.
Since I love Chromebooks, I wanted to write an article about how these two vulnerabilities affect them.
This isn't a deep technical review about Meltdown or Specter. There are loads of well-written articles about them. Instead, I will just lightly explain it to the general public.
These 2 are bugs in the design of the processor (aka the brain) of your computing device (made by Intel & AMD). These "bugs" have existed for about 20 years and allow an attacker (capable of running code on your system) to break security controls implemented on systems and in apps to steal information. Specter does affect your smartphone (probably).
Great detailed information about these can be found here for those who are interested: https://meltdownattack.com/
Google has a support article that clearly outlines its plan to ensure all Chromebooks are eventually patched.
But how do I check my device?
First, check the version of ChromeOS you are running. Most should be at version 63 already and this partially fixes some of the issues. You can check if your product has an update available here.
The good news is that most mainstream devices are patched including:
- Google Pixelbook 2017
- Samsung Chromebook Pro
- ASUS Chromebook Flip C302
Some even say "patch not required" like:
- Samsung Chromebook Plus
- Acer Chromebase
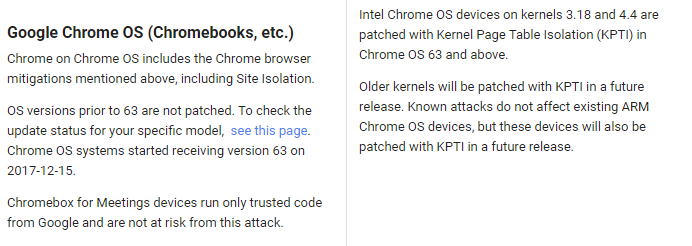
Systems with kernel 3.18 or 4.4 are already patched. you can also use the chrome://gpu flag and search for operating system to find your kernel level.
Google's position is that ARM-powered Chromebooks and Chromeboxes are not vulnerable but will be patched anyway with future updates.
How is Google fixing the issue? With something called Kernel Page Table Isolation (KPTI). Basically, they are separating the kernel memory from that of the user processes.
The moral of the story? Security is a hard computer science problem but you should sleep much better tonight (compared to Windows or Mac users) knowing that Google is working feverishly to protect you from these types of attacks. Just make sure you are using a supported product and reboot when you see the little upward arrow indicating there is an update (in the lower right hand status bar).