What is GrandCrab?
GrandCrab is a successful ransomware that encrypts files on the infected machine and demands payment to decrypt them.
Easy Money
What is you are a horrible human being willing to make gains from the suffering of others but you are lazy. You want to screw other people but don’t want to spend the time setup your own Command and control server? You don’t want to customize the malware to talk to your C2 server?
This is where Ransomware as a Service comes in.
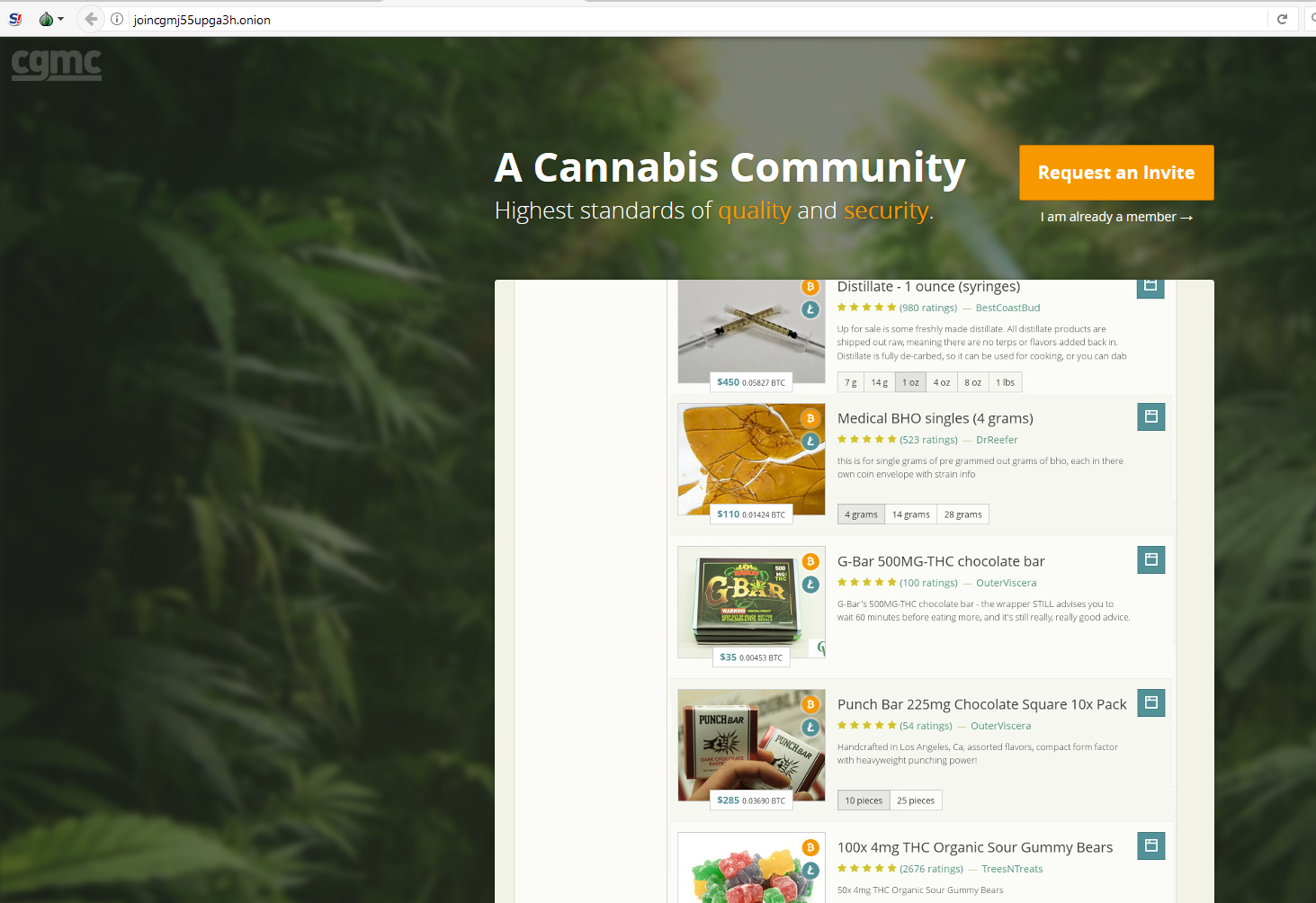
Enter GrandCrab as a Service http://gandcr4cponzb2it.onion/
The offering
The GrandCrab RaaS has two tiers:
Standard at $230
Premium at $600
Standard Service
You can change and customize your ransomware
Name of the project
Change the demand of ransom
A description to help the victim in format .HTML, .PHP
You can change the logo, Remove GandCrab logo
You can choose the extension for example photo.png.gdb
Priority support
Automatically updated since the category (Ransom Builder)
The victim can pay you in Bitcoin or Dash
Withdrawal in Bitcoin or Dash
We will touch 10% fees ransom
You can add 3 users different free
You can create 3 ransomware
Victims can you contact by chat directly, you can also ban
You will have news about the dashboard
Geolocation victims infected
Show the IP of the victim
Manage the keys of decryption
You will be able to manage all the victims since the dashboard
With several possibilities
You can infected in unlimited
You can see the blockchain explorer
Spreading automatically without providing any effort or you can also spread manually
You will have full access to our forum with the rank Platinum (forum under construction soon available)
Victim URL automatically generated in .onion customize your own URL
View antivirus report in real time
Lifetime license !
Theme only white
Premium Service
The same features different even more fun
You receive 100% of the ransom paid by the victims no commission fees
Ransomware automatically updated by our support
Victims can you contact by chat directly, you can also ban
Spreading automatically without providing any effort or you can also spread manually
The victim can pay you in Bitcoin or Dash and Monero !
Withdrawal in Bitcoin, Dash, Monero
Automatically increases the ransom if no payment of the victim
Choose your own delete time
Create up to 10 different ransomware
You can add 8 users different free
Make the ransomware in format .pdf
bulletproof hosting, server VPN
Priority support by ticket since dashboard
Change all the logo, An icon in format .ICO, Remove the gandcrab logo, Add an animated logo in .GIF
Manage all the victims since the dashboard
You will have a fully functional 2019 tutorial to teach you, In format .pdf .mp4
Assignment on multiple computers in seconds from the same WIFI network
Undetectable by antivirus update regularly
Victim URL automatically generated in .onion customize your own URL
You can infected in unlimited
Manage the keys of decryption
Change the theme ransomware
You can see the blockchain explorer
Geolocation victims infected
You can also see the operating system
Show the IP of the victim
You will have full access to our forum with the rank Gold (forum under construction soon available)
You will have the ransomware source code, contact us from the dashboard with your login only for premium members
View antivirus report in real time
Crypter fud
Lifetime license !
Theme dashboard white, black
Conclusion
The conclusion is that security is hard and hackers are learning about the benefits of offering “things as a service” and using cloud to reduce costs. Attacking is become cheaper while protecting our organizations is becoming more costly