A podcast is a great way to consume a large amount of new information in a short period of time. Every week, I listen to dozens of podcasts that cover topics such as tech, security, news, economics, psychology, and more. In the past year, I have been bombarded with host read advertisements sponsored by NordVPN and ExpressVPN. Many of these hosts are reading copy that is unreliable at best or purposefully misleading at worst.
This article aims to clarify misinformation regarding privacy improvements directly related to VPNs.
TL;DR: A VPN alone does not provide adequate privacy
The following article is intended for a general audience. Professionals in Information Security can devise solutions that incorporate VPNs to provide the level of privacy and security required by their customers (based on the customer's specific risk profile).
More Details
If you are not paying for a product or service, then you are that product. You should never utilize a free VPN service. Operating a VPN service is expensive, so they must recoup their costs somewhere (and they will probably make a large profit selling your information to data brokers).
The downside of a VPN is there are dozens of ways it can fail you, but you should understand that you are shifting all of your traffic through the VPN (which means if they are breached or decide to sell your data, they may have access to everything). Perhaps you do not want your large ISP to be able to see your Internet traffic, but would an unnamed VPN provider be any better?
The truth is that while many companies claim to operate on a zero-log basis, there is no way for a user to determine this for certain. Several providers have failed to meet their zero-log promises, resulting in a user being profiled or arrested.
Tracking you
Dozens of hosts are simply reading ad copy provided by the advertiser, and I have heard similar ads on dozens of other podcasts.
The first question is a valid one: would you prefer your ISP to view all of your traffic or the VPN provider. Despite the fact that most people dislike their services with the passion of a thousand suns, at least you have an understanding of what they are doing. I would trust only a few VPN services more than my Internet service provider.
The majority of websites now utilize HTTPS/TLS, which creates an encrypted tunnel between a user and a website. As an example, if you are using HTTPS/TLS to access Facebook (which is now the default), your ISP will know you visited Facebook and how long you spent there, but they cannot see what you did nor can they inject traffic info that flow or modify it in any way.
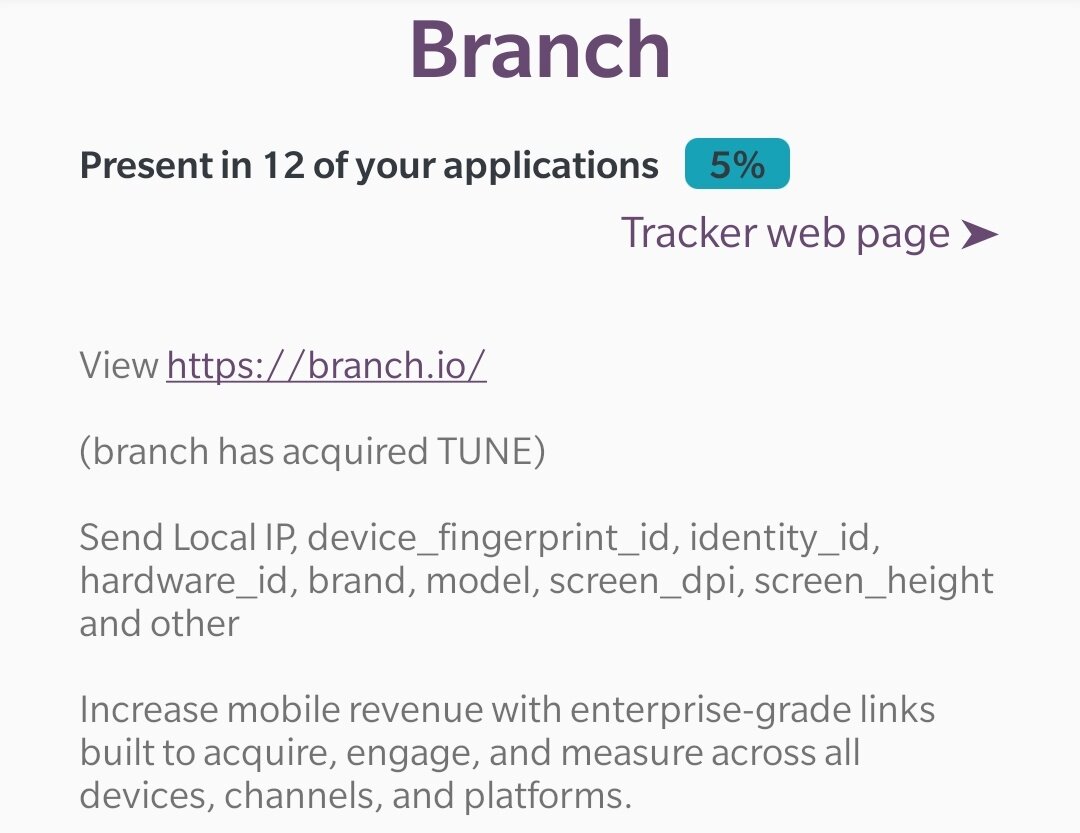
The other fallacy is that information brokers or large social media sites require your IP address in order to track you. VPNs do conceal your origin IP address, but very few trackers still rely on it to identify you. In addition, they take into account other factors, such as the operating system, plug-ins, display size, and resolution. Any website that has a Facebook-like button shares traffic information with Facebook. Any site using Google Analytics shares information with Google.
Use the EFF's Cover your Tracks website to find out how identifiable you are.
Alternatives
Option 1 - Apple PrivateRelay
Rather than using a general-purpose VPN, most users would be better served by configuring their browser security and using Apple's PrivateRelay (it's not perfect, but it's more secure than VPNs for the average user).
Option 2 - TOR
Tor remains the best alternative for someone that wants maximum privacy. TOR is free, open-source and trustless. It will be slower and you won’t be able to stream music or videos but it a good tool for someone looking to augment their privacy on the internet.
Option 3 - Break censorship
You may wish to consider using the censorship-busting VPN service called Psiphon if you are in an environment that uses technical controls to support its censorship efforts.
Conclusion
As soon as your packets hit the VPN provider's boundary gateway, the provider strips all encryption and then retransmits your data based on the technology available on the site (where you are browsing). HTTPS/TLS will be secure, HTTP/FTP will be insecure.
A VPN was originally designed to protect a company's data while its employees were working remotely. Consumer VPNs were a secondary market, and by default, VPNs are not designed to be log-free. Providers of VPN services must devise solutions in order to make their service more private by using technologies such as RAM-only servers, configuring the VPN to delete log files, etc. It is crucial that they have a sound architecture and that they deploy this architecture correctly without errors to protect your privacy.
Although VPNs remain useful in some situations, they are not the magic bullet that will allow the average (non-technical) user to become private. It is simply a tool that allows a tech professional to design an appropriate security program based on the risk profile of the user.
For the average user, the only good use of a VPN is to stream multimedia content that is geo-restricted (such as Netflix, Hulu, Peacock, etc.).