Bitcoin is a decentralized digital currency, without a central bank or single administrator, that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. Bitcoin was invented in 2008 by an unknown person or group of people using the name Satoshi Nakamoto, and started in 2009 when its source code was released as open-source software.
Bitcoin is often called the first cryptocurrency, although prior systems existed. Bitcoin is more correctly described as the first decentralized digital currency. It is the largest of its kind in terms of total market value.
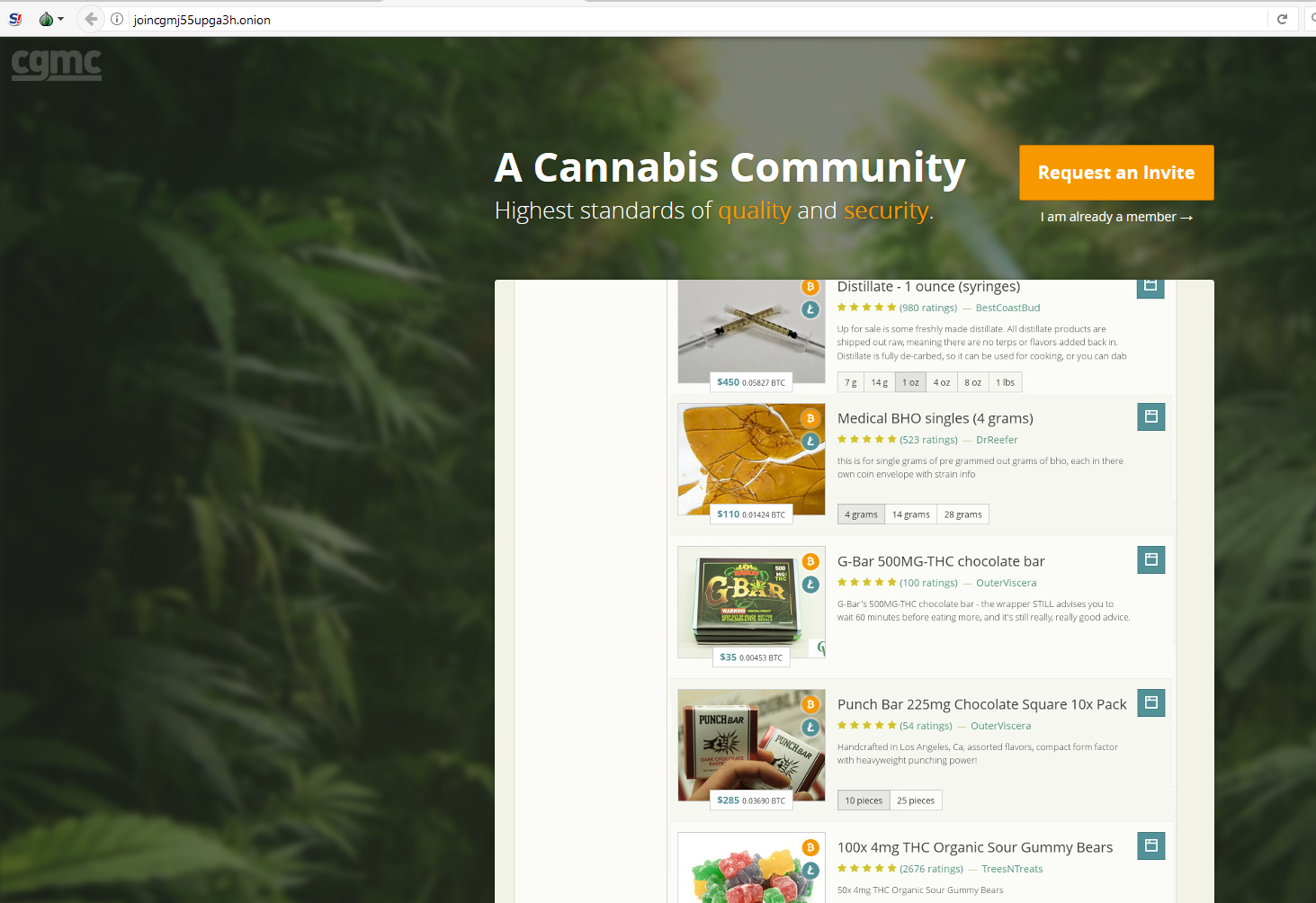
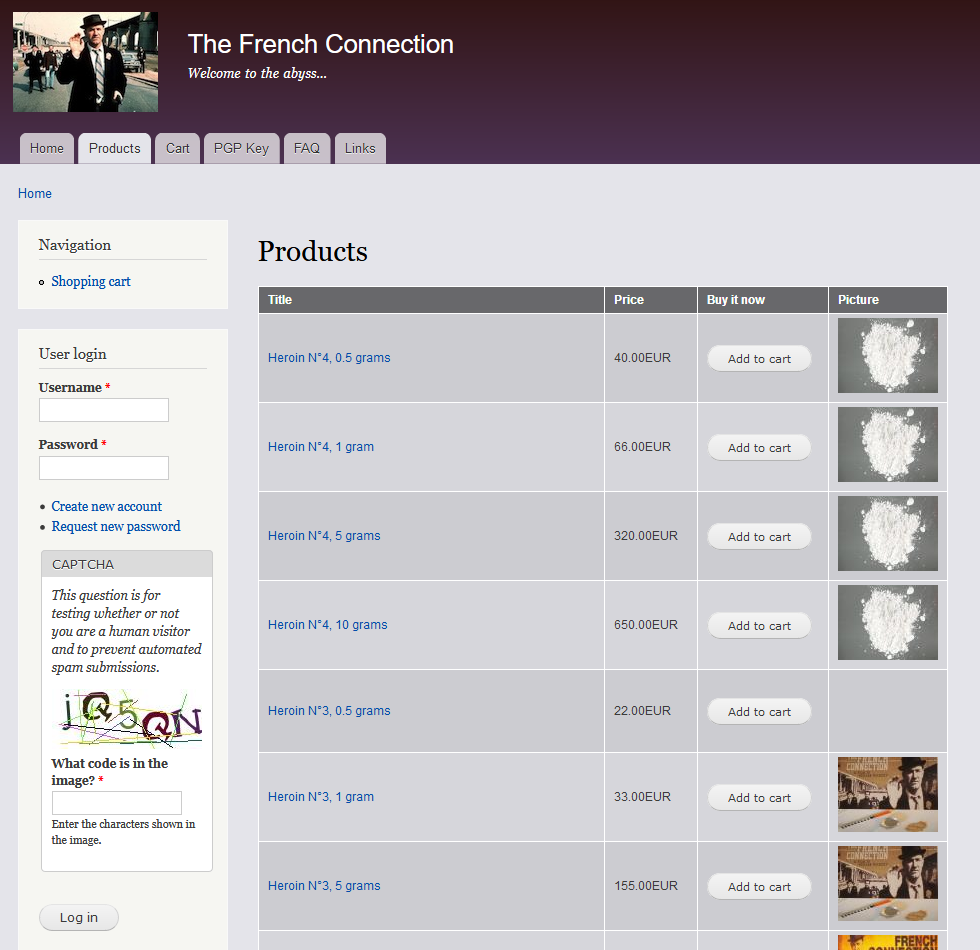
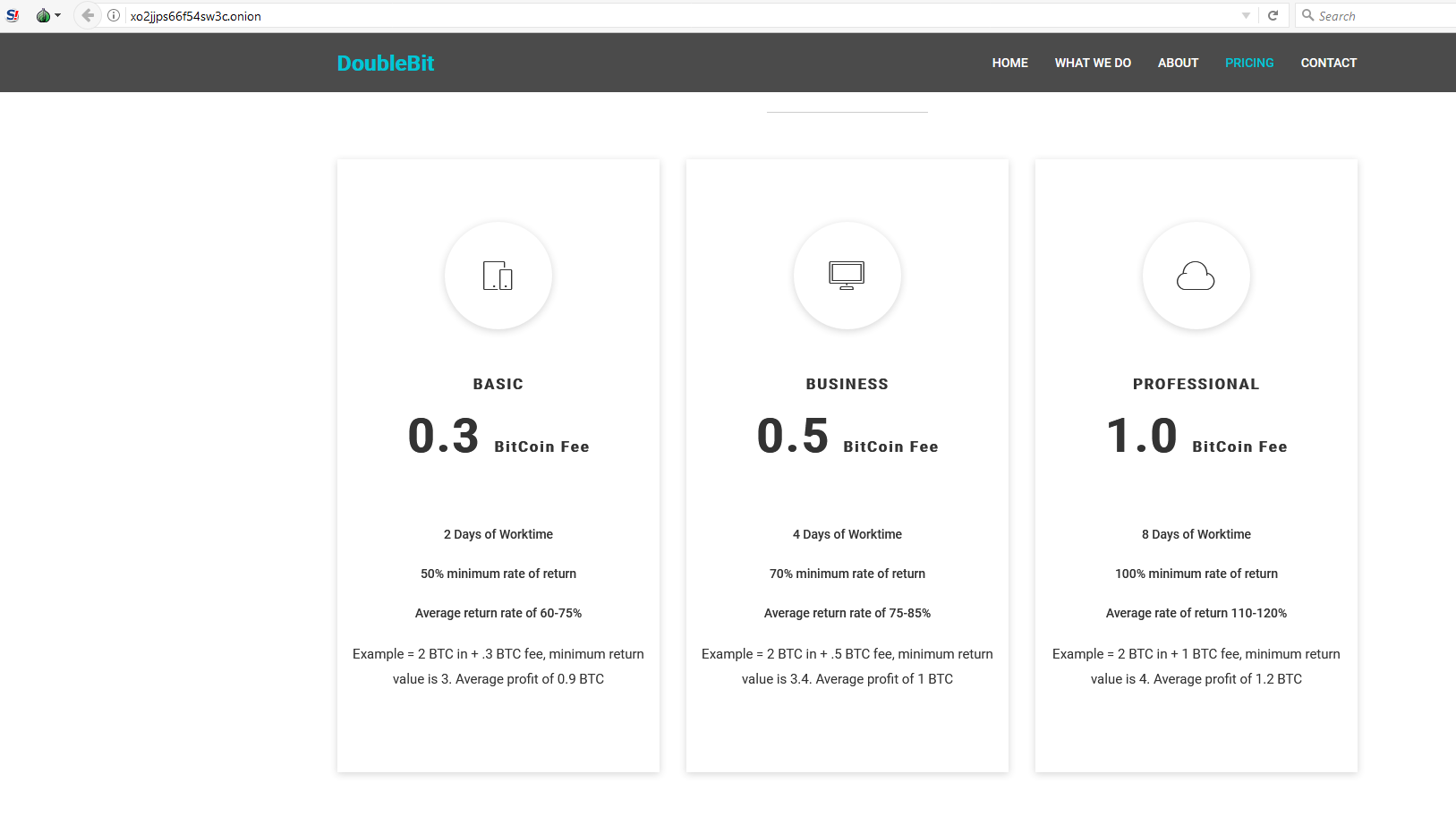
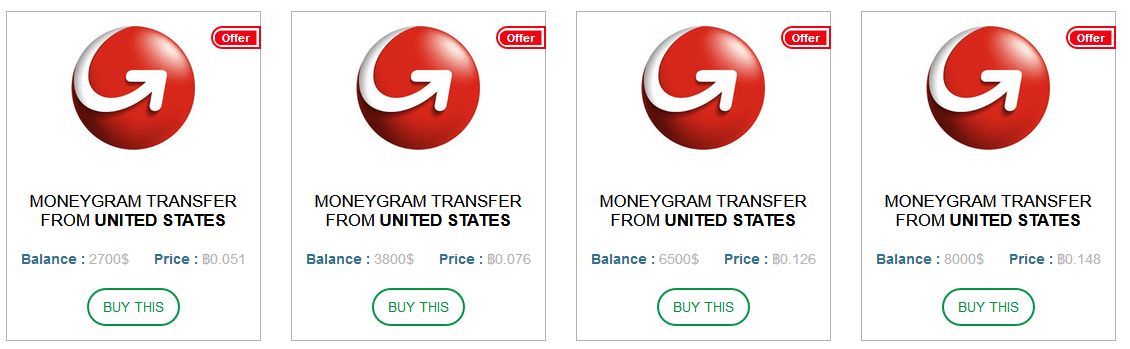
Bitcoins are created as a reward for a process known as mining. They can be exchanged for other currencies, products, and services. As of February 2015, over 100,000 merchants and vendors accepted bitcoin as payment. Bitcoin can also be held as an investment. According to research produced by Cambridge University there were between 2.9 million and 5.8 million unique users using a cryptocurrency wallet, as of 2017, most of them using bitcoin.
What is proof of work?
Proof of work is a system that is used to secure the Bitcoin network. Miners are rewarded with bitcoins for their work in verifying and committing transactions to the blockchain. Proof of work is also used to ensure that new blocks are added to the blockchain in chronological order and not randomly.
In order for a new block to be added to the blockchain, miners must solve a complex mathematical problem. The difficulty of this problem varies depending on the total amount of computing power that is being used to mine Bitcoin. When more miners join the network, the problem's difficulty increases, and vice versa.
Why do environmental groups have a problem with proof of work?
Environmental groups have a problem with proof of work because it requires a lot of energy to power the computers that are used for mining. In fact, according to one estimate, the amount of energy required to mine Bitcoin is more than the annual energy consumption of the country of Ireland.
This has led to concerns that proof of work is not sustainable in the long term and that it could have a negative impact on the environment. However, there are some proposed solutions to this problem, such as using renewable energy to power the computers used for mining or using proof of stake instead of proof of work.
What is proof of stake, and can it solve the environmental problems?
Proof of stake is an alternative to proof of work that is used to secure the Ethereum network. Miners are not rewarded with bitcoins for their work but instead earn a share of the transaction fees that are collected by the network.
This system is seen as more energy efficient than proof of work, as it does not require powerful computers to run the mining process. However, proof of stake is still in the early stages of development, and it is not yet clear if it will be able to scale to the same level as proof of work.