Why would anyone use Protonmail instead of Gmail or Hotmail? SECURITY
Email is inherently insecure and if you are a political dissident whose online communications can mean the difference between living and dying, don't use email. For everyone else looking for an easy and secure email solution, keep reading about Protonmail.
“Everyone needs to understand that SMTP was not designed to be secure and will always have security weaknesses.”
We use email because we don't have a choice and everyone agrees it won't be displaced tomorrow.
The other major issue faced by secre service providers is ease of use. PGP is a good example of strong unbreakable email encryption that never became mainstream because it was simply too complicated for the mortal man.
“Absolute security is unpractical and will never gain widespread adoption so good security should be the goal for most services.”
There is always a tradeoff between usability and security, The difficulty is finding the right balance.
So what does Protonmail offer?
The bright scientists behind Protonmail understand fine balance they must find between usability and security. Make the product too secure and no one will use it (aka bankruptcy) or make it extremely user friendly but not secure (become a me too email provider).
They have chosen to implement good enough security which makes encryption generally accessible to the masses while protecting against unauthorized government seizure or mass surveillance.
What are the weaknesses of Protonmail?
Read my blog post about the Vault7 leaks (here) and you will realize that when government is stifled by strong encryption (Whatsapp, Signal, etc), they compromise the endpoint and extract the information pre/post-encryption.
Protonmail does not protect you if your endpoint is compromised. It would be unreasonable to assume any secure online service could protect you from this type of attack. if you want maximum endpoint security, learn about real security protocols and use a secure operating system like Qubes OS.
Nation state level man in the middle attack. Protonmail implements all of the controls to prevent a common man in the middle type of attack but a nation state actor with the ability to redirect your web traffic and generate real "fake" TLS certificates could theoretically intercept your traffic, ask you for your username/password then use those to access your account and decryption keys. Let's be clear that your garden variety hackers (even those that are extremely skilled) won't be able to pull this off. This would require skills, money and huge technical capabilities to reroute internet traffic and generate encryption certificates.
Intelligence break in. With all the talk about government backdoors, the third major weakness of Protonmail (and all other secure services products you did not write) is the fear that a nation-state actor would somehow infiltrate Protonmail and then implement "special" code that sends bad encryption code to the users thus allowing the threat actor to access unempted versions of the messages. Protonmail has stated that they have multiple controls in place to protect against this type of attack. They scan servers for unauthorized code changes.
Some nice features of Protonmail
Protonmail is a Swiss company based in Switzerland. Any government request for information would have to be done there using Swiss law, which is very protective of private information (USA cannot issue a National Security Letter to force the company to turn over information and hide the request from the user).
In the rare situation that a government were to spend the money and convince the Swiss court to compel Protonmail to turn over user information... Protonmail uses "Zero Access Cryptography" which means they do not hold the encryption keys and therefore can only turn over encrypted information.
Protonmail supports (and you should use) 2-factor account authentication. This means that in addition to something you know (your username and password), you need something you have (a time based authentication code generated by an authentication app Google Authenticator or Authy.)
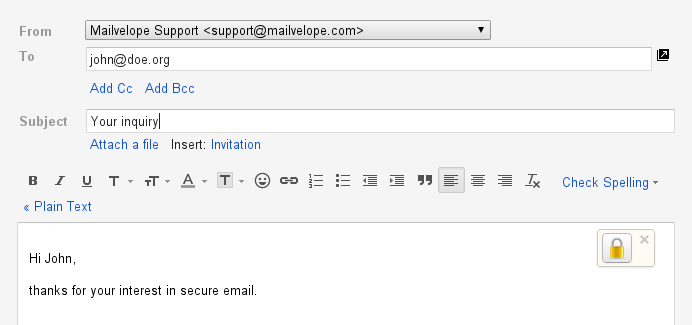
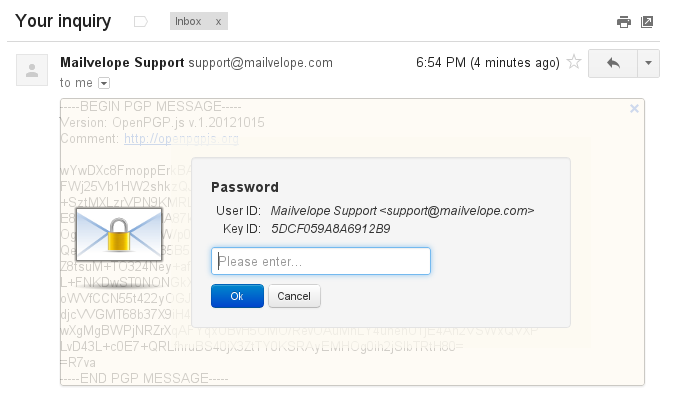
If you want to send something more secure than normal email to a non-Protonmail user, you can create a Protonmail hosted message that requires a password to open (obviously don't send the password using email) and can even have a fixed expiry date.
Creating a password for the secure "hosted" email
Setting an expiry time for the message
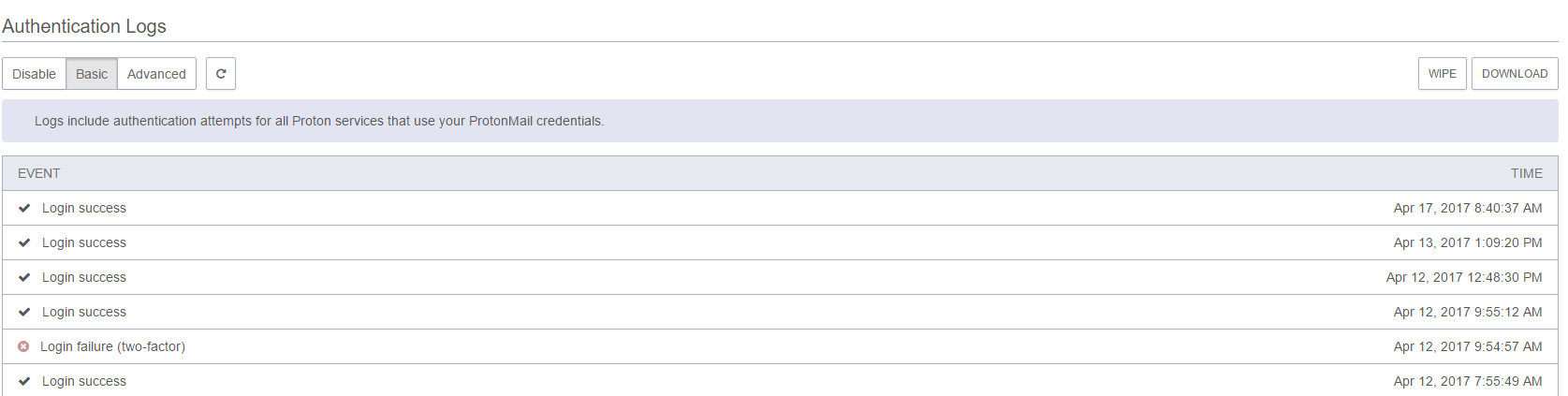
Protonmail stores user based encrypted authentication logs. This means you can see when your account was logged into and from which IP address. You can turn this off it you don't want this captured. Protonmail does not capture or log your IP anywhere else.
The ProtonMail service has internal authentication logs. When I say internal, I mean that these details are available only to the account owner, and are recorded and encrypted with all the other data inside the account. As I mentioned earlier, Proton Technologies AG doesn’t log IP addresses, but this information can be logged inside your web client session. If you don’t need them, just wipe the logs and switch to basic mode which doesn’t record info on the IP addresses you logged in from.
Basic stores login dates / times only. Advanced also stores the IP Address from where you logged in. The choice is yours. You can always download this information or secure erase it.
No user profiling. When you use a free service, the provider is conducting deep analysis and creating a deep analysis about you. Protonmail doesn't do this since everything is encrypted.
They encrypt all non Protonmail emails received immediately upon ingestion.
“Emails that come from third party email providers obviously cannot be delivered with end-to-end encryption, but upon reaching our mail servers, we will encrypt them with the recipient’s public key before saving the messages. All this is done in memory so that by the time anything is permanently stored to disk, the email is already unreadable to us. ”
This is good for security but limits what they can do for SPAM control. In a blog post, they explain what they do to help fight SPAM:
- They check the IP address of the incoming SMTP server against known blacklists
- They pass all messages through their own Bayesian filter marking suspicious emails as SPAM
- They generate a checksum for each email message and verify this checksum against known SPAM messages
- They verify the authenticity of the email using standard protocols (SPF, DKIM and DMARC)
Sending secure emails to non Protonmail users
I alluded to this earlier but wanted to restate it here in it's own section since I would otherwise receive a dozen emails asking this question.
“Can secure emails be sent from Protonmail to non-Protonmail uers (Gmail, Hotmail, Outlook, etc)?”
When sending emails to non-Protonmail users, you can:
- Send an un-encrypted standard email. This is what every other email provider does.
- You can use the lock icon in the compose window which asks for a password (See screenshot earlier in this post). In the case this is set, the recipient will receive a message with a link to a Protonmail web interface and he/she can use to enter the provided message password and see the email.
Notification non-Protonmail user receives
Password requested by non-Protonmail user.
Free versus paid
Protonmail offers a free basic tier and I recommend everyone start with this level. If it meets your needs, you should consider upgrading to a paid tier which offers custom domains and more storage.
Conclusion
I love Protonmail and am moving my private (not public) email address there. I like the security it provides and the open philosophy they espouse. I say use them if you want something more secure and private.
You may also want to read my article about SpiderOak. SpiderOak is a Google Drive, Microsoft OneDrive or Dropbox alternative with strong trust no one encryption.