Read this related article: Find phishing and malware with a simple search
Search engines have become a favourite starting point for threat actors, so it should also be your starting point. Beyond Google, there are a bunch of specialized search engines that are powerful and scary. This article talks a bit about Shodan. Think of this article as a gentle introduction.
What is shodan
Shodan is often called the world's most dangerous search engine. Shodan attempts to catalogue metadata about its targets and its targets are often Internet of Things (IOT) devices. Hackers and security researches use Shodan daily to find vulnerable webcams, open traffic light systems, SCADA in manufacturing plants and much more.
I'm going to assume you have a free Shodan account.
Browse the categories
If you visit the Shodan Explore section, you can find all kinds of interesting systems listed.
Unprotected webcam
For this example, I searched for the Axis 212 webcam which is known to have many vulnerabilities and a known default password.
As an example, the webcam I highlighted seems to be in a daycare facility and isn't even password protected.
I've blurred out the children and teacher.
Some are unprotected. Some have kept their default passwords (there are lots of default password lists like this one). Obviously many of these cameras are made by a handful of manufacturers in China and are never updated. Once you find a vulnerability on one model it is often workable on dozens of others.
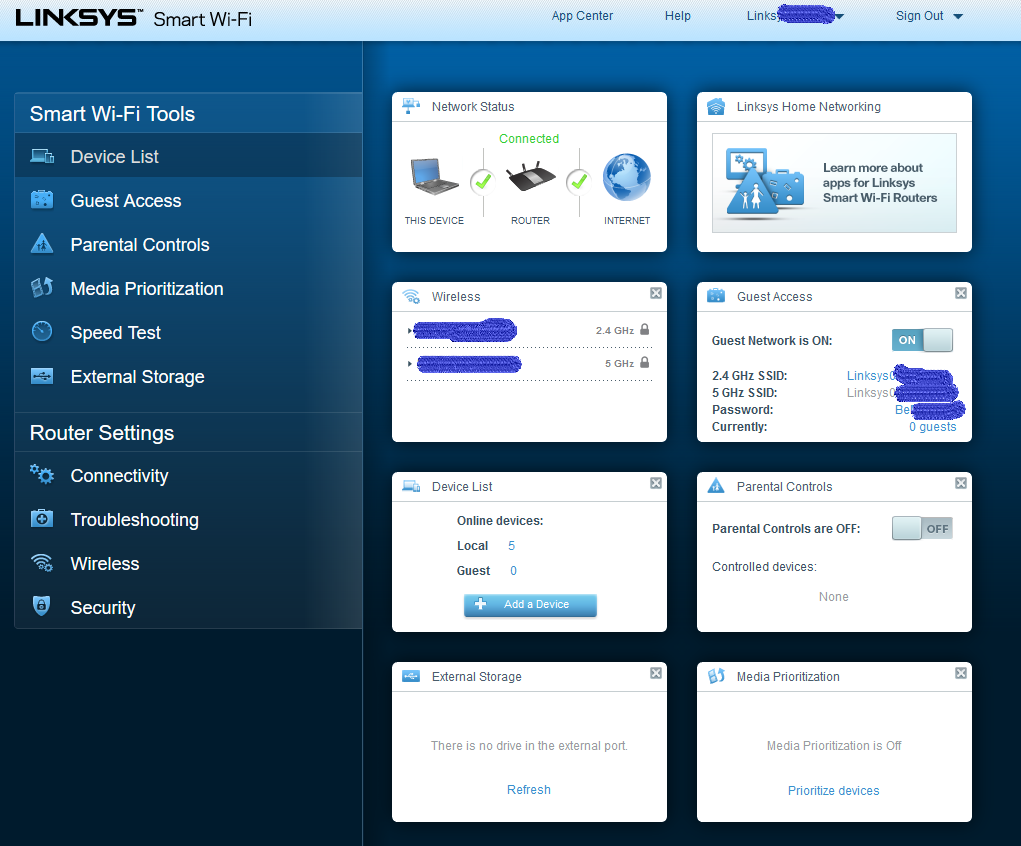
Routers
You can search Shodan for common router brands like Belkin, D-Link, Netgear, etc and then try to log in using the default admin passwords. Above is an example of a Linksys router exposed to the internet without a password. Others are exposed with the default password.
Intel AMT Exposed to the internet
There is a major Intel AMT vulnerability but Shodan shows that 4,647 devices with AMT (on July 22) were connected to the internet.
If you search for "http intel active management" in Shodan, you will get a listing of these devices.
Other searches you can perform
Netgear device with port 80 open to the internet
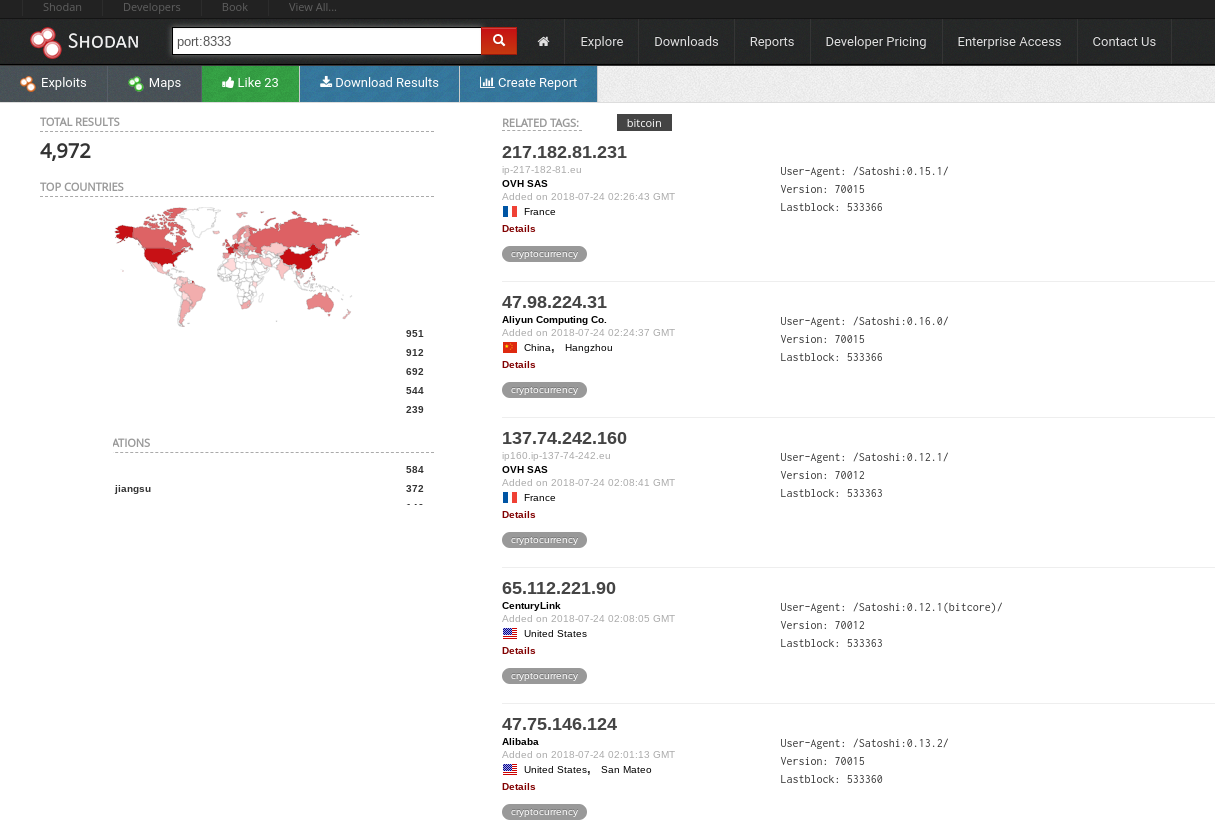
Bitcoin servers
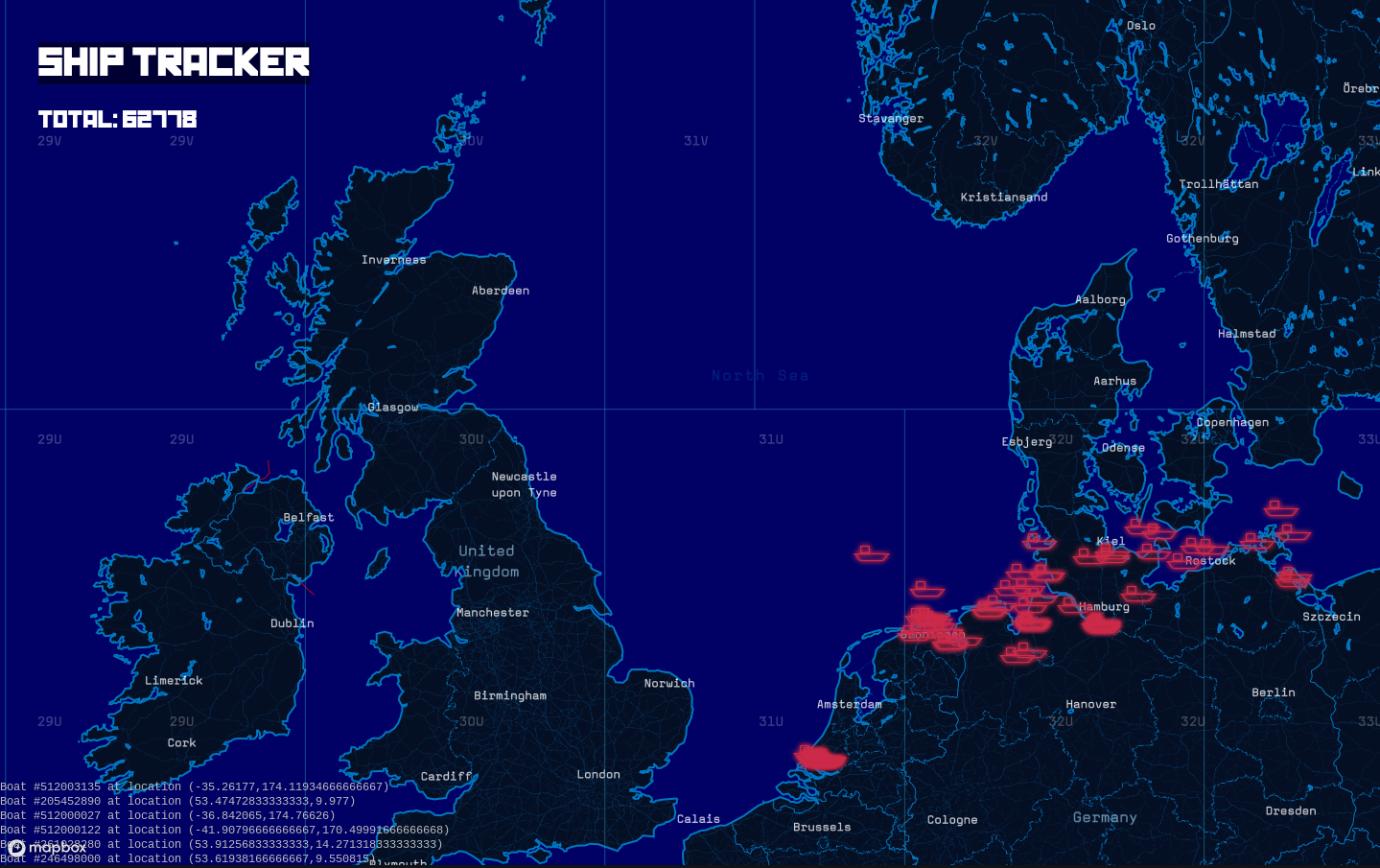
You can even use the Shodan ShipTracker dashboard to track realtime ship
ShipTracker is harmless on its own, but combined with data available from other sources and the knowledge that many ship systems use default passwords and it is a disaster waiting to happen.
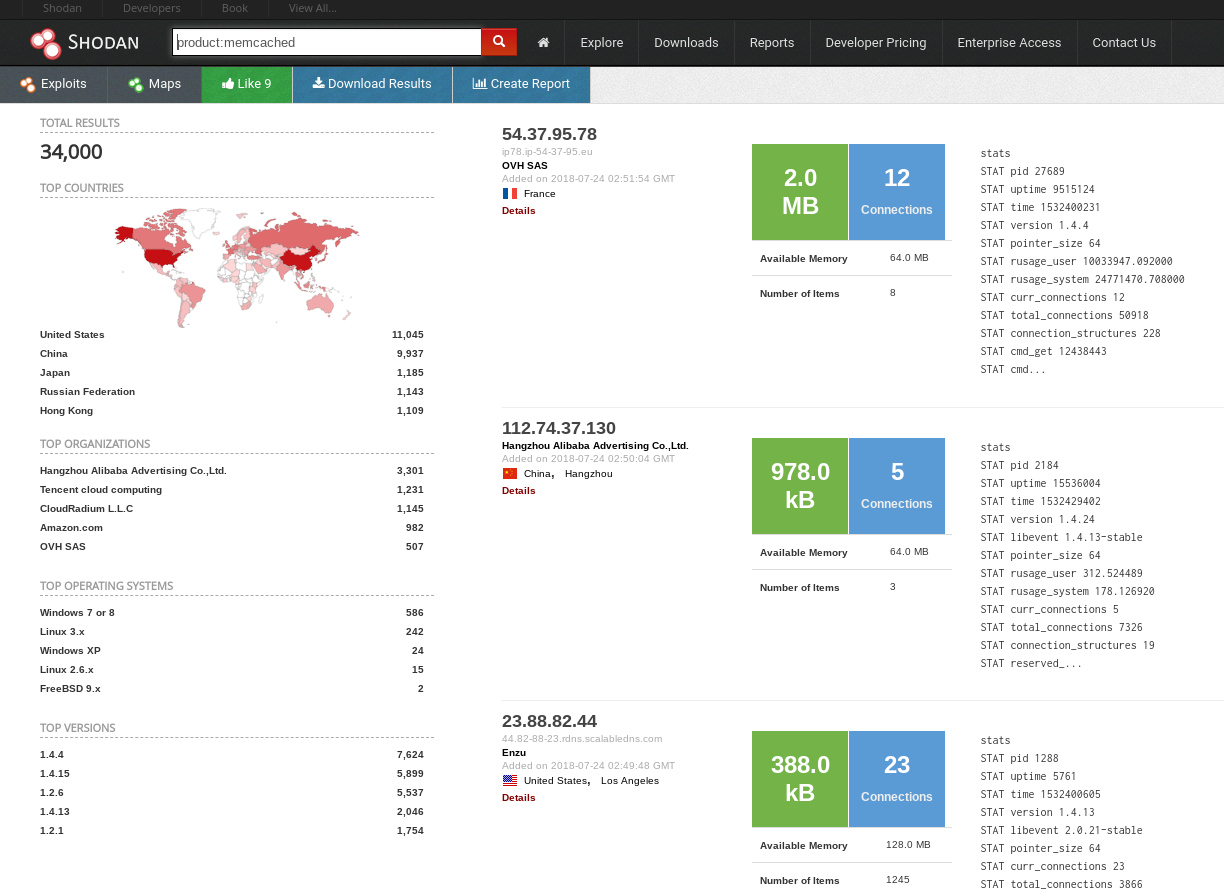
There is a known vulnerability that allows a threat actor to steal or modify information from a Memcached server. This vulnerability was used to target GitHub with a massive DDoS attack. Not all Memcached servers are vulnerable ( I won't show you how to find the vulnerable ones) but how would you search for Memcached servers on the net? The answer is with a Shodan query.
Conclusion
Obviously, this is just the tip of the iceberg. A true threat intel specialist will be able to automate Shodan queries and then combine them with known vulnerabilities, exploits or default credentials. I am hoping this article created a bit of interest in you to learn more.
For this article, I only chose examples that were exposed to the internet and were not password protected. Be careful as laws differ around the world. In some countries even testing default passwords could be considered "hacking".