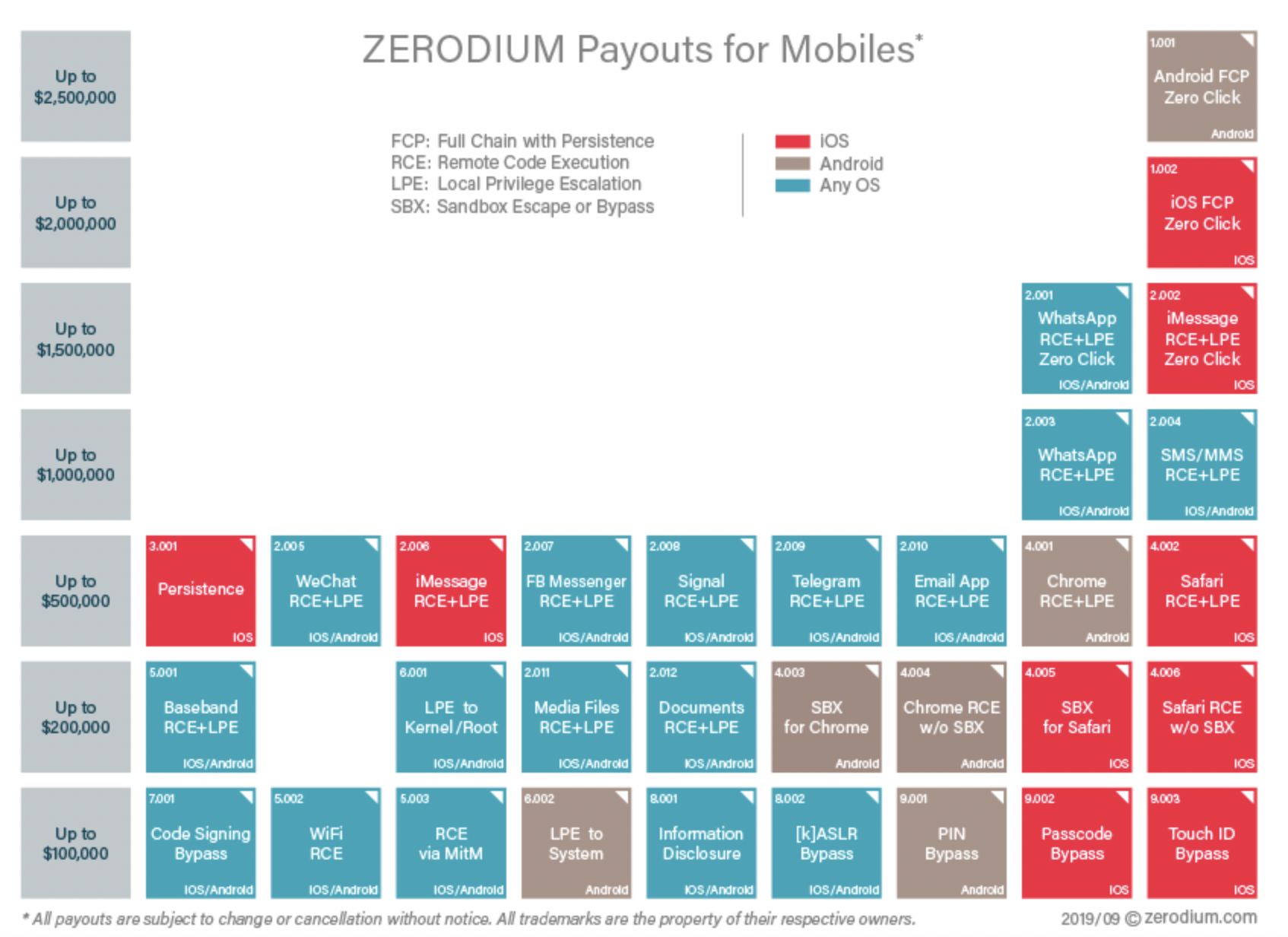
The free market determines pricing based on the intersection of supply and demand. For the longest time, an IOS Full Chain Compromise with Persistence (FCP) demanded a significantly higher payout from vulnerability vendors than Android ones. This was a simple question of economics: Android had more easily exploitable vulnerabilities thus each one was worth less. On the other hand IOS was built like Fort Knox. Vulnerabilities were few and far apart and dictatorial regimes and evil doers were willing to write much bigger checks to buy those rarer exploits.
The chart above shows the pricing as of April 2 2021 and clearly shows that an Android FCP demands a $500,000 bonus over an IOS one. We know demand for these has not dropped so the only possible explanation is that there are more IOS vulnerabilities in the market than Android ones.
Although Google doesn’t use security to market its smartphone OS, it has a best-in-class security team that is making Android more secure with every release. IOS is improving as well but not as fast as Android.
Before you start throwing things at me, remember that privacy and security are two very distinct qualities. There is no question that IOS offers a fairly secure computing environment and world class privacy.
Android on the other hand asks you to trade in some privacy in exchange for a super functional assistant but has done a fantastic job making it’s operating system more secure.
Speaking with a security consultant buddy that advises many large companies and special interest private organizations about operational security, he confirms that the “underground” demand for FCP android vulnerabilities is skyrocketing. He mentioned that patched Android vulnerabilities are becoming harder to find but that the demand is skyrocketing (because so many of his customer targets use the lower cost android platforms"). Zerodium isn’t the only vulnerability broker in the market but it is the only one that publicly publishes its payout tables.
My contact said Android’s open source nature is yielding many of these security benefits (e.g. Google regularly upstreams security improvements made by AOSP fork operators like the GrapheneOS).
The bottom line is that these operating systems are typically weakened by bad user decisions (configurations, app choices, etc), but out of the box, Android running on a Pixel device is probably more secure (but less private) than IOS.
The challenge on Android is the fact many phone vendors do not offer timely upgrades (if ever) which makes these phones super vulnerable. That is why if you use Android, stick with a Pixel device with guaranteed security upgrades for 3 years and OS upgrades for 2 years.
We know Apple invests heavily in security so we’ll have to see what security improvements, if anything, Apple implement in IOS 15.