Quietly and with little fanfare, Whatsapp released an update to all of its products enabling end-to-end encryption for its 1B+ end users. Funny enough, most users aren't aware that their Instant Messaging tool of choice is now powered by the worlds most secure end-to-end encryption protocol : Signal.
Can I consider WhatsApp secure?
A couple of weeks ago, OpenWhisper systems announced that its Signal secure protocol has been imbedded into Facebook's WhatsApp instant messaging application. The question I receive daily is "should I consider my Whatsapp communications protected now?"
Before signal there was OTR
Before using the Signal protocol, it looks like the WhatsApp team evaluated the OTR (off the record protocol). OTR provides encrypted point to Point communication but it requires a real time collaboration of the users (aka both have to be online to secure the transmission) which isn't practical for WhatsApp. So they went fishing for something else and stumbled upon Signal.
The Signal difference
Signal actually created an encryption model using the text messaging approach, where messaging is encrypted but it is asynchronous (both parties don't need to be online simultaneously for it to work).
Although text messaging is simple, the complexity of the encryption is model is high.
The protocol was called axolotl. The salamander it is named for has self healing capabilities and the axolotl protocol also has self healing properties.
To simplify it for mass consumption, the procotol was renamed the Signal protocol and now has open source libraries. Cryptogrsphers have been able to build fully function encryption programs comptible with the consummer Signal apps.
Now powering Whatsapp
The integration is now complete in the latest version of Whatsapp on all platforms.
Users running these versions now get full end to end encryption for every message they send and every Whatsapp call they make. All the benefits of the signal protocol are now built in.
We have confidentiality which means the communication is encrypted.
We have integrity which means message alterations will be detected and fail the verification transaction.
Authentication is possible (which is good) but you need to take extra steps to do so. Keep reading.
Participant consistency is also important but defaults to off (has to be enabled manually).
They also claim to have destination validation, which requires the above 2 to work, so technically it is available and built in.
They have forward secrecy which means a future compromise of a private key will not allow the decryption of past messages.
They have backward secrecy, which means a past compromise of a private key will not compromise future protected communications. Keys are constantly being changed and re-negotiated.
They have message unlinkability, which means messages are independent, asynchronous, can arrive independently or be missing, without affecting the fucntioning or efficiency of the entire system.
Message repudiation is also there, which means the sender can deny sending a message. This works because the receiver can forge a message that looks like it came from the other party. Which means none of the participants can claim (to a 3rd party) that a message originated from the other party with verifiability. All that can be claimed is that the sender or the recipient sent the messages. To most this seems bad but in the world of security, this is a good think.
Simple but complex
We all know Whatsapp is a simple to use product but the actual encryption is very complicated and therefore beyond the scope of this post.
As an example, they create static Diffie Hellman encryption keys. Then they create a set of ephemeral keys. Then they use a triple Diffie Hellman protocol to exchange their ephemeral keys and they use a Diffie Hellman key agreement 3 times to take their private key and the other person's ephemeral public key and create a key agreement.
The other user takes his private key and the other persons Diffie Hellman public key to create a second agreement. Then they take the ephemeral keys and use that with Diffie Hellman to get a third set of keys and they concatenate all of these together to create a master session key.
The ratchet
In an interactive protocol a ratchet is where you evolve a key that you agree upon as you send messages back and forth. You ratchet the key forward.
The problem is that this requires real time communications. The innovation here is that they developed an offline ratchet using a hash. Each time both parties are online at the same time, an online ratchet is performed and resynchronize the offline ratchet hash.
First sessions establishment
In real time communications you can create a shared key in realtime. But how do you do this is an asynchronous model with someone you have never messaged before?
To solve for this issue, when you register your Whatsapp client with the server, your client pre seeds the server with 100 ephemeral public keys and assigns an ID to each. This means someone wanting to send you a message for a new communication stream, picks up one of those keys in order to bootstrap a secure message.
They use this public key and place it back on the server until you are online. When you come online, that blob is sent back to you. Your client will never allow the re-use of that public key (by removing it from the pending ephemeral key list). This one time use prevents certain types of attacks.
Perfect encryption
Knowing that Moxie (from OpenWhisper systems) worked on it and reading all the documentation, it looks like they implemented a perfectly designed asynchronous encrypted messaging system.
The one caveat & other thing
The one major exception is that you cannot be sure who you are talking to (authentication).
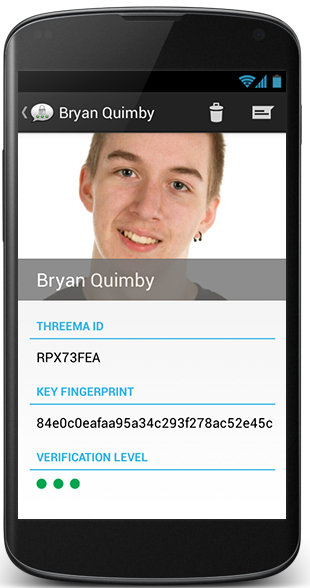
Threema, my favourite truly perfect encrypted and private messaging system, solves this by only guaranteeing authentication when you physically scan the QR code of the other participant's public key.
To solve this, Whatsapp provide a (per communication thread) QR code or 60 decimal digit user verification code. This code contains both parties encryption keys.
So the problem is you need to perform this verification at least once per conversation thread. This guarantees there is no middleman. Where you can't visually exchange codes, you can read the 60 digit code to each other. If the codes are different, it means there is a man in the middle.
For some reason if the codes change, you are not automatically notified. But under account security, you can enable this notification.
Go to Settings, then Account, then Security, and ensble the switch
Everyone needs to turn this on (participant consistency). The only time a code should should change during a conversation is if the other party installs the app on a new device (or a reset device), in which case you will already likely know and can disregard the alert.
I also want to remind readers that although the messages themselves are encrypted, there is still metadata. There is no technological way to communicate without leaving a trail of metadata today. Metadata is data about your data : such as who you communicate with, how often and how much data you exchange with each other.
Whatsapp is not open source
Many security researchers dislike closed source security applications because there is no way to independently validate the implantation (aka. Know for sure that no one has implemented a back-door or injected malicious code.)
Technology is only as good as its implementation and although the encryption math is perfect, applications rarely are. At some point we have to put our crazy hats down and trust that companies are tying to do the right thing for their users.
Conclusion
Facebook has done a very good job and with the flip of a switch, they have gifted 1B people with easy to use and powerful encryption. I still love Threema because it has better authentication but the truth is none of my contacts use it.
I am excited that more people will be brought into the wonderful world of encryption and have their discussions protected.