The last couple of articles I wrote referred readers to TOR (darknet/darkweb) sites. These sites are easy to identify because the terminating marker is .onion (instead of .com/.net/org).
The right way of accessing TOR sites is with the secure TOR browser designed and distributed by the TOR project. This purpose-built browser uses a hardened firefox to deliver maximum anonymity while browsing the "normal" web or tor sites.
There may be times when you are on a device that doesn't have the TOR browser and when speed is more important than privacy or security. In these situations, web-based services allow you to browse these tor (.onion) sites from a standard browser. That is the purpose of this blog article.
The following sites are web services that will allow you to access tor sites without using the tor browser (using a normal browser like Chrome, Firefox or Safari).
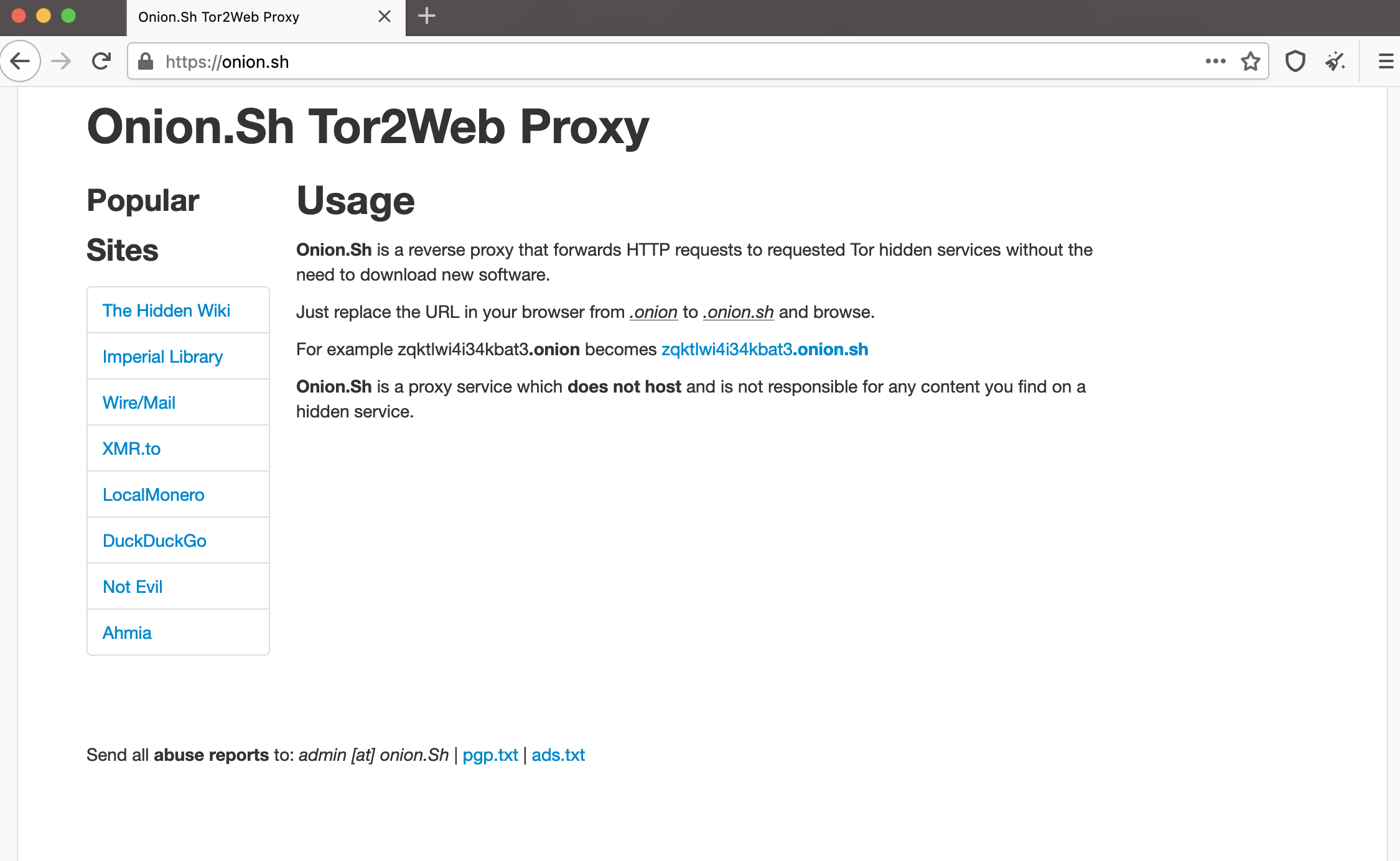
These services are called TOR gateways or TOR proxies. the TOR2WEB project was designed to allow users to access all onion services without using the TOR browser. The project site is here.
Remember that using these gateways means the gateway operator can see where you are going, and you lose all privacy and anonymity features of TOR.
To use use TOR2WEB gateways
Using most sites is very simple, you take your TOR address
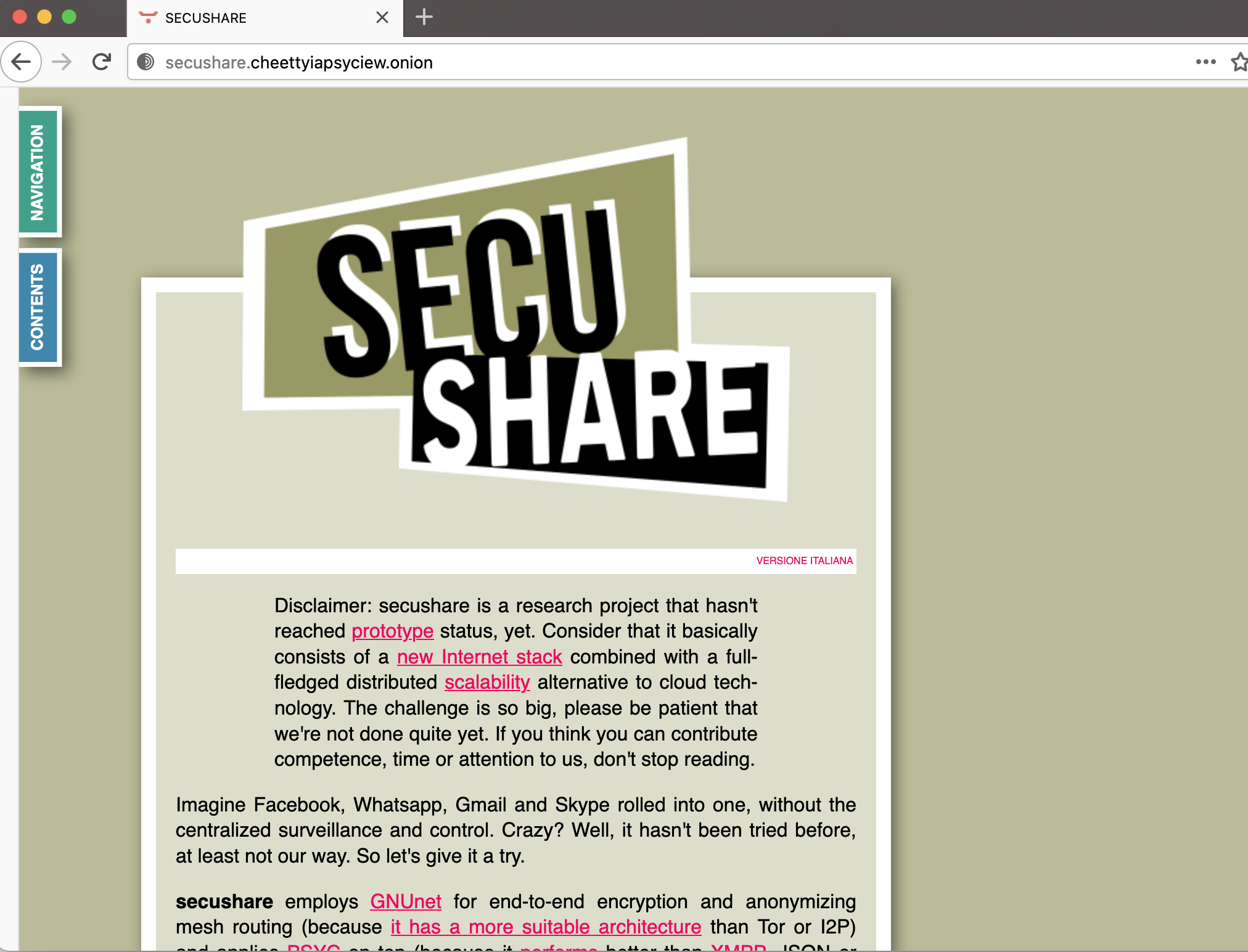
Here is the secushare onion service at http://secushare.cheettyiapsyciew.onion/
you append the gateways domain name to the end of the onion address. As an example, if you want to use the gateway called onion.ws you simply add .ws at the end of the URL like this
http://secushare.cheettyiapsyciew.onion.ws
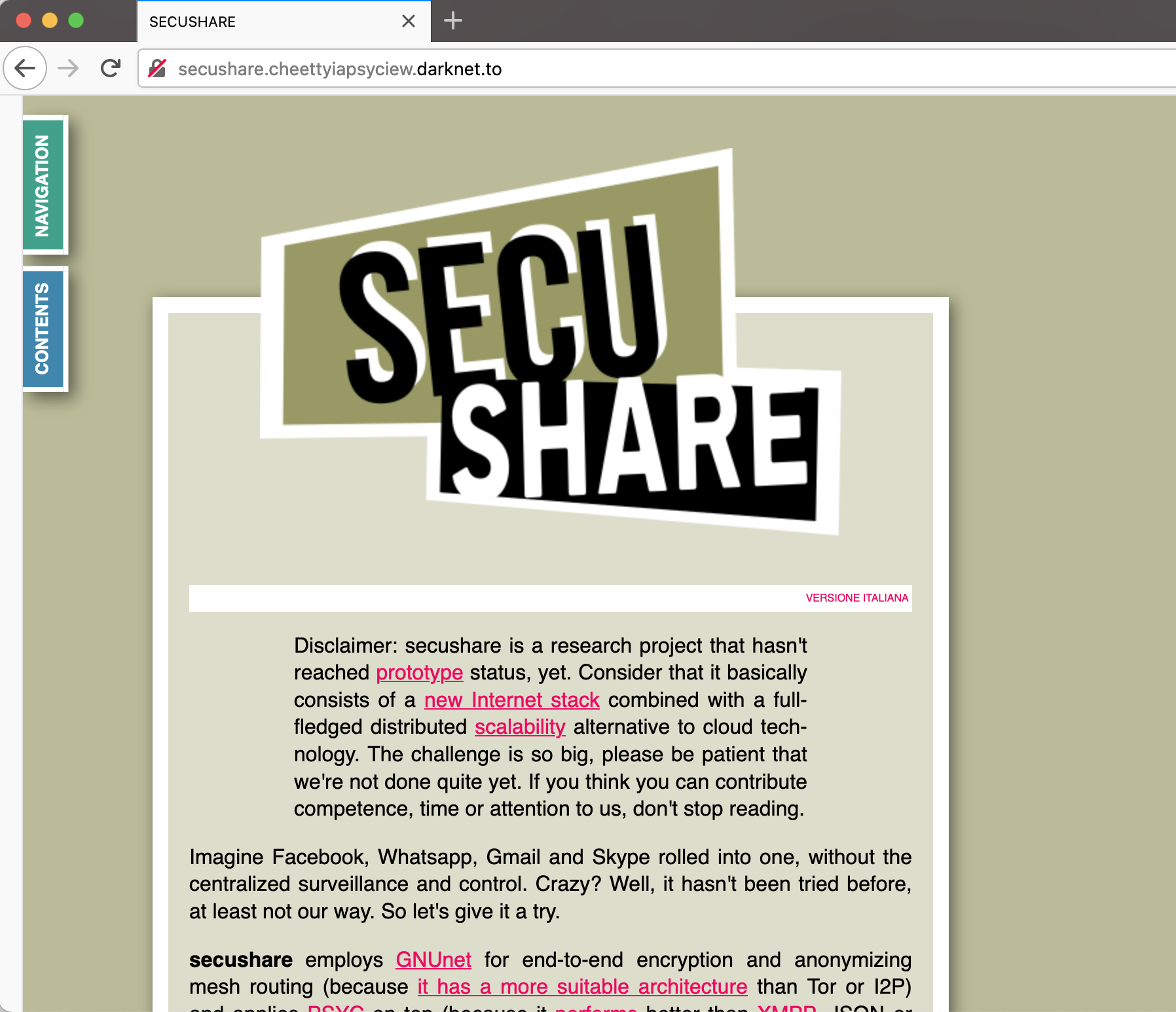
Some rare ones require you to remove the .onion at the end and replace it with their gateway url (e.g. like darkness.to) the above address would need to be
http://secushare.cheettyiapsyciew.darknet.to
List of TOR2Web gateways
Be aware as free services, many of these sites are flaky and will periodically be down. Try another one or try later.
If you visit the main domain with your browser, most will provide instructions (in case you forget how to use them)
New sites pop up everyday so if these sites don’t work for you, just search for tor2web gateway in your favourite search engine (startpage.com, duck.com, etc)
Warning
I mention above to only use these services when security and privacy aren’t a concern. You may be wondering why. Here is a list
Session leakage
This is the same risk you experience when using any VPN service. Because the service is the one routing you to your final destination, they see everywhere you go and everything you see. A malicious operator can log and record your entire session with all traffic send back and form (between you and the TOR service). Never enter login credentials (or anything personal) when using these gateways.
Service enumeration
When using the TOR browser with long random TOR URLs, your browsing is relatively private. When using these gateways, you are on the “normal” web and any dns server used by your browser will see the URL you are visiting (e.g. http://secushare.cheettyiapsyciew.darknet.to)
Assume any DNS in your configured DNS chain or the providers chain will know what URL you are trying to resolve through your TOR gateway service.
User correlation
When using these gateways, the gateway operator can log all of your publicly available user identifiers (IP address, browser, OS, fingerprint, etc) and then log that you visited X tor site.
Conclusion
Although these gateways aren’t considered secure, there is a use case for them and it is another tool in your online tools arsenal. If you use them knowing their limitations, you will be fine and they could save you a lot of frustration.