Embrace digital transformation: Utilize cutting-edge technologies such as artificial intelligence, machine learning, and automation to streamline processes, improve efficiency, and generate new ideas.
Keep your employees trained and updated: Foster a continuous learning and upskilling culture to ensure your team stays ahead of the curve and adapts to ever-changing business conditions.
Focus on Customer Experience: Utilize data-driven insights to understand the needs and preferences of your clients and deliver personalized experiences that exceed their expectations and foster brand loyalty.
Use Agile Methodologies: Increase your organization's adaptability and responsiveness by adopting Agile practices, such as Scrum or Kanban, allowing you to pivot and iterate based on market feedback quickly.
Enhance Your Online Presence: Develop engaging content, optimize your website for search engines, and maintain an active presence on relevant social media platforms to drive traffic, generate leads, and establish thought leadership.
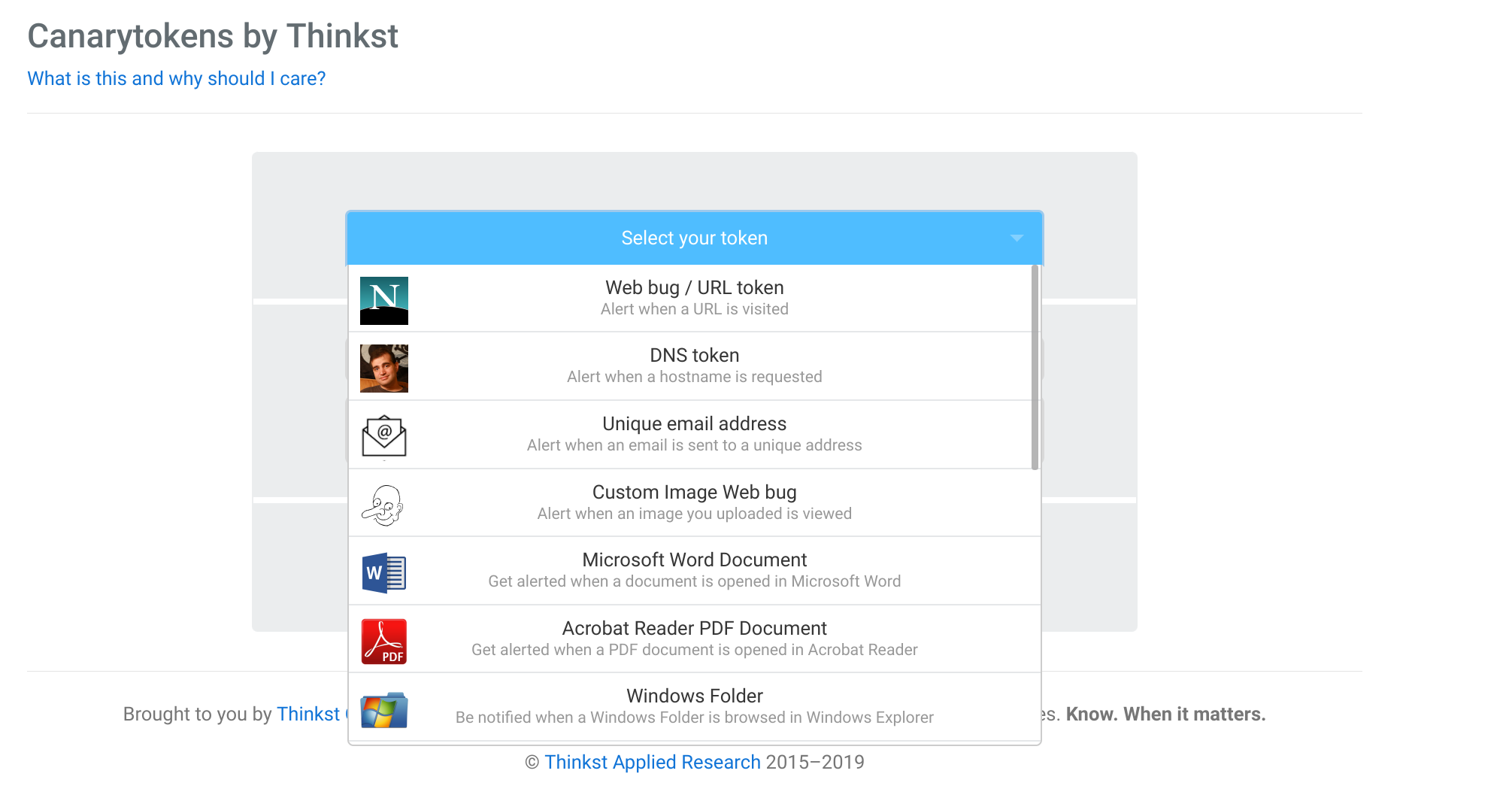
Data Security and Privacy: Establish robust cybersecurity measures and privacy policies to safeguard sensitive business and customer information.
Take advantage of networking opportunities: Attend industry events, conferences, and trade shows, and engage with influencers and thought leaders in your niche to create valuable connections and stay on top of the latest trends and opportunities in your industry.
Track Key Performance Indicators (KPIs): Establish clear, measurable, and achievable objectives for your business and monitor KPIs regularly to assess progress.
#BusinessSuccess #DigitalTransformation #EmployeeDevelopment #CustomerExperience #AgileMethodologies #OnlinePresence #DataSecurity #Networking #SMARTGoals #KPIs