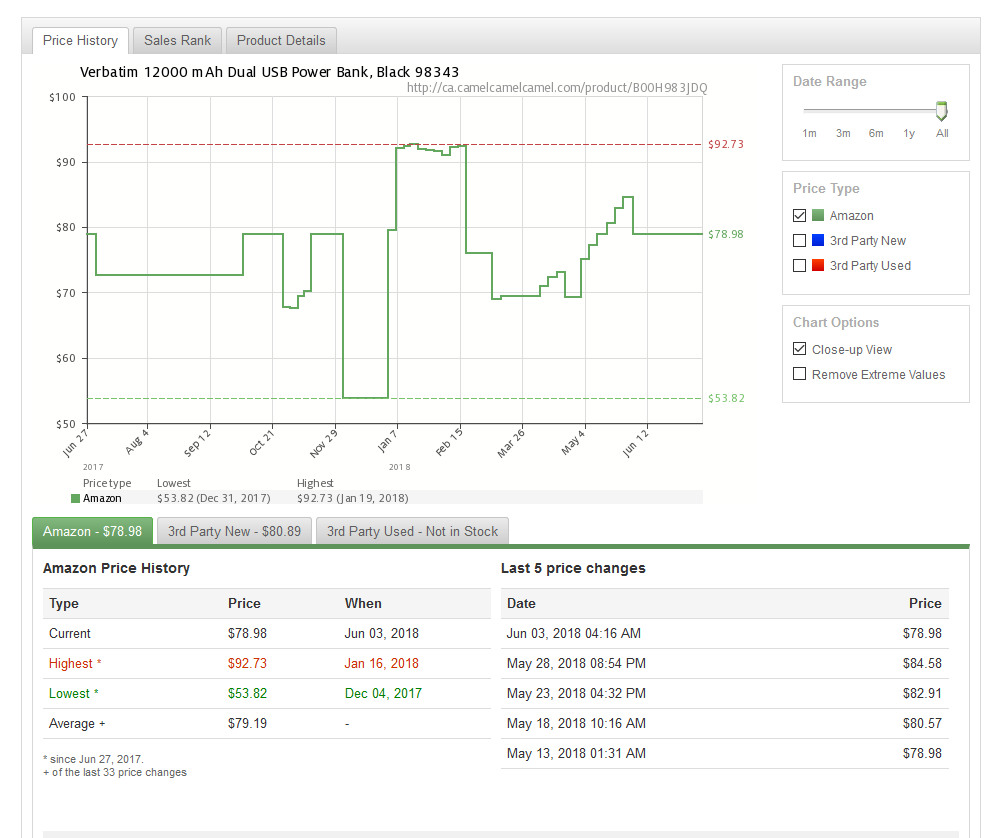
A captive portal is the intercept page you see when trying to log into most free public WIFI hotspots (e.g. airport, restaurant, hotel, etc.) You are normally shown a page that collects your email and then asks you to agree to the provider's terms of conditions.
As browsers adopt more secure protocols by defaults (iPhone, Android, Windows, Mac, iPad, etc.) there are situations when your device may not trigger the portal webpage correctly. The browser may block redirection to the portal page because it is typically transmitted using unsecured HTTP.
In some cases, devices will attempt to detect and open an unencrypted webpage to allow the public WIFI router to inject a redirect URL. WirelessPhreak has a good technical article that discusses why new more secure tech is causing this issue.
Each smartphone manufacturer uses a different non-SSL webpage to detect a captive portal:
- Google Android: http://connectivitycheck.gstatic.com/generate_204
- Apple iPhone & iPad: http://captive.apple.com/hotspot-detect.html
What do you do if that automated portal detection doesn't work? How to you trigger the captive portal?
Enter the webpage Never SSL. If you are connected to a public WIFI (that should work) but are not seeing the captive portal, open your browser of choice and navigate to http://neverssl.com/
This will fix your issue and you should be bathed in warm loving WIFI Internet.