Security and usability are contradictory forces. Ultimate usability means less security and ultimate security mean less usability. It is a fine balancing act tat every user must perform themselves.
The iPhone is a well designed and fairly safe device out of the box but there are some settings you can change to reduce your odds of getting attacked. Each setting that you change will make your device a bit more secure but will limit a useful functionality.
This article will walk you through some of the settings that will reduce your susceptibility to software exploitation.
Install patches
Your iPhone should be configured (out of the box) to periodically download software and OS patches but you should check manually every day (to ensure you get the patches as quickly as possible)..
Don’t open that attachment or that link
Although the iPhone has a very mature and sophisticated security model (including sandboxing), we have seen advanced threat actors use zero-day attacks sold by vulnerability merchants to attack freedom fighters, journalists and other people of interest.
Like on a traditional computer:
never open an attachment from an unknown person
never open an unexpected attachment from a known contact
never click through on a link (SMS, Whatsapp, Telegram, Twitter, Facebook, Instagram, etc) from an unknown person
never click through on a link from a known contact but an unexpected message
Reboot your device
We have seen many sophisticated and advanced attacks performed against iOS devices that leverage unknown (therefore unpatched) vulnerabilities but many of them are not persistent. This means that the attacker has to re-compromise your phone if they want control, after a reboot. Think of the reboot as a cleanse or detox.
This has become a standard ritual for me and I regularly restart my phone throughout the day.
Pay attention to the dots
Apple has implemented an ingenious feature to quickly show you if an app is using your camera or your microphone. When in use, an orange or green dot will appear on your top menu bar next to the battery indicator.
An orange indicator means the microphone is being used by an app on your iPhone. Remember that if you are legitimately using this for features like Siri, it is normal that this will show up but it should disappear when you are done or it means something is still listening in (legitimate or not).
A green indicator means either the camera or the camera and the microphone are being used
If you swipe Control Center open, on the top, it will show you the last app that triggered the microphone or the camera
Disable Airdrop
Airdrop is an Apple technology that allows you to quickly and easily share content (files, videos, music, links, etc) between IOS and macOS devices. AirDrop itself could have vulnerabilities that could allow an attacker to send a malicious attack file to your device without your knowledge or they can perform social engineering attack to trick you to click on a malicious file.
Swipe up (on older phones) or down from the right-hand side of the screen (on modern devices) to show the control center
3d touch or long-press the network settings card (in the upper left-hand corner, then click on AirDrop)
Choose Receiving Off to disable AirDrop
Disable Bluetooth
Bluetooth has had many easily exploitable vulnerabilities in the past. Although Apple quickly patches vulnerabilities, there may be unknown vulnerabilities being sold by vulnerability merchants to threat actors or nation-state attackers. Additionally many organizations (from law enforcement to shopping mall managers) are known to track users with their Bluetooth ID.
If you are not actively using Bluetooth (aka connected to headphones for example) then you should consider disabling it. Disabling it will cut off the connection between your phone and Apple Watch (until you turn it on again).
Swipe up (on older phones) or down from the right-hand side of the screen (on modern devices) to show the control center
Click on the Bluetooth icon to turn it off
Disable JavaScript in Safari
JavaScript powers the modern web but has been used in a significant number of web attacks. Disabling JavaScript will significantly improve the security of your device but will likely break many modern websites (rendering them unusable).
If you are a higher-risk individual (politician, journalist, dissent, etc, then you may want to turn JavaScript off. Otherwise, you may want to ignore this change (aka leave it on). Changing this setting only applies to JavaScript inside of the Apple Safari web browser.
Open the Settings App
Find Safari
Scroll to the bottom until you see Advanced
Turn of JavaScript by tapping the toggle switch.
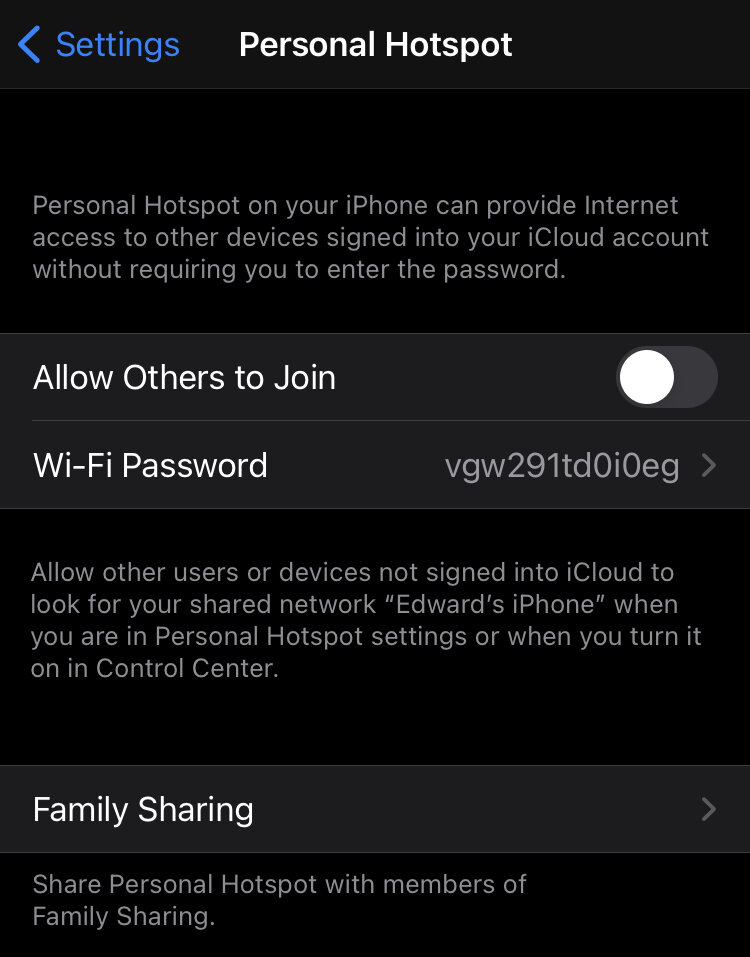
Disable WIFI Hotspot
The WIFI Hotspot is a setting that is normally set to off. I am specifying it here in case you turned it on.
WIFI hotspot allows other WIFI devices to connect to your smartphone and share its LTE connection (3G, 4G or 5G). Obviously, those devices need to have the WIFI Hotspot password that is configured on your smartphone, but it is possible iOS contains a vulnerability not yet known by Apple that could be exploited, this allowing a threat actor to connect to your device and push malware.
Open the Settings App
Open Personal Hotspot
Turn off Allow Others to Join