Learn about the top 10 free OSINT resources for junior SOC analysts. Discover tools for threat detection, incident investigation, and cybersecurity analysis to enhance your organization's defense capabilities.
In the digital age, organizations across the globe are increasingly concerned with the security of their networks and data. Among the critical aspects of modern cybersecurity is Open Source Intelligence (OSINT), which entails collecting information from publicly available sources for use in a security context. A proper OSINT tool can assist in the detection of potential threats, the investigation of incidents, and the improvement of overall security posture. Below are the top 10 free OSINT resources ideal for junior Security Operations Center (SOC) analysts.
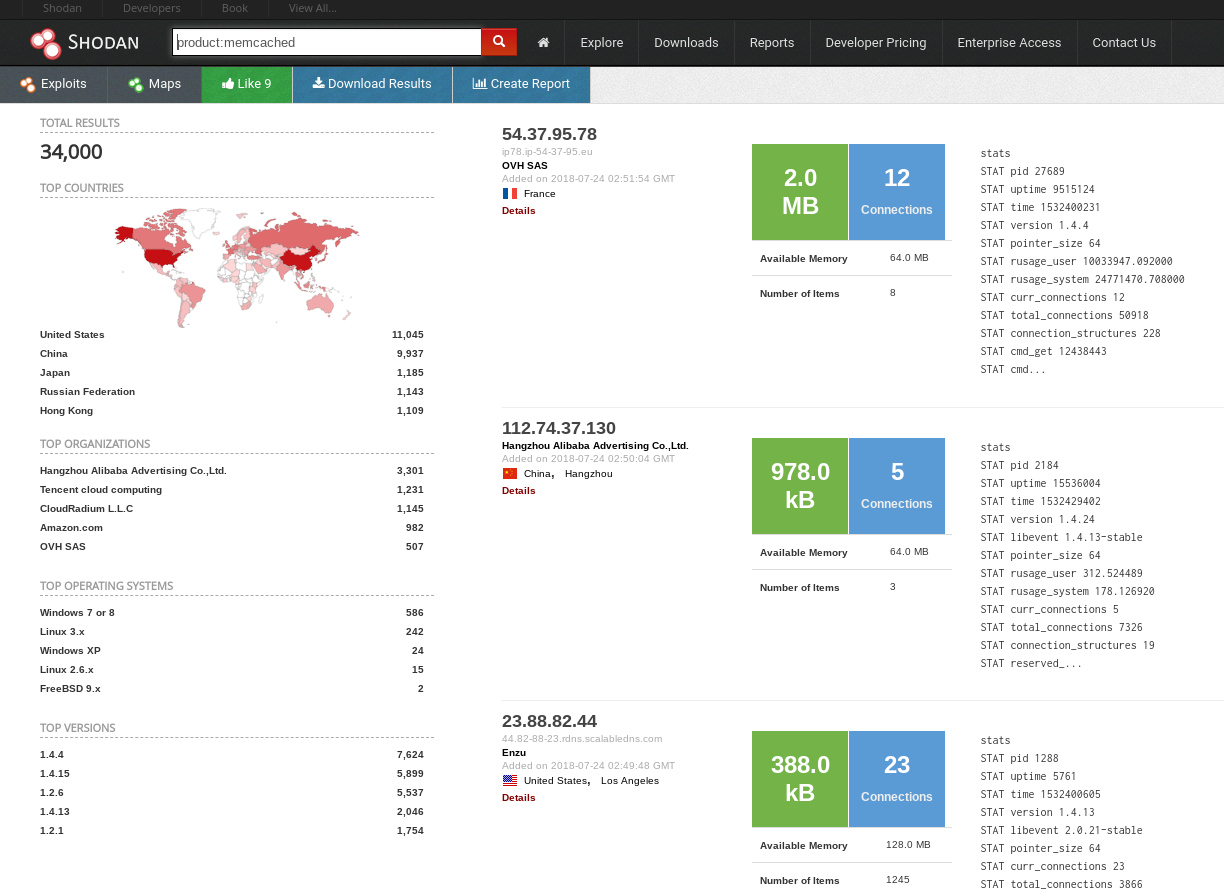
Shodan (https://www.shodan.io/): Shodan is a search engine for internet-connected devices, which can be used to find information about servers, routers, webcams, and more.
VirusTotal (https://www.virustotal.com/): VirusTotal is a service that analyzes files and URLs for viruses, worms, trojans, and other malicious content detected by antivirus engines and website scanners.
Have I Been Pwned (https://haveibeenpwned.com/): This site allows you to check if an email address has been compromised in a data breach.
Censys (https://censys.io/): Censys is a platform that helps information security practitioners discover, monitor, and analyze devices accessible on the internet.
Google Dorks (https://www.exploit-db.com/google-hacking-database): A collection of Google search queries to identify vulnerabilities, find servers, and discover sensitive data.
OSINT Framework (https://osintframework.com/): This tool is a collection of OSINT resources, categorized and sorted for easy navigation, covering a variety of information types and sources.
PublicWWW (https://publicwww.com/): PublicWWW allows you to search the source code of millions of websites, which can help identify sites with similar code, structure, or elements.
AlienVault OTX (https://otx.alienvault.com/): AlienVault OTX (Open Threat Exchange) is a crowd-sourced threat intelligence platform where security professionals and enthusiasts can share, research, and collaborate on emerging threats.
Whois Lookup (https://whois.domaintools.com/): Whois Lookup provides a way to determine who owns a particular domain name, including information such as the owner's name, contact details, and when the domain was registered.
Intelx.io (https://intelx.io/): Intelx.io is a cybersecurity search engine and data archive, providing access to various datasets, including the dark web, domain registrants, and more.
As we conclude, these top-tier OSINT resources provide a powerful gateway for detecting and investigating cyber threats and proactive cyber defence measures. Since they are free of charge, they are an excellent opportunity for budding SOC analysts to hone their skills and expand their arsenal of security tools. A proactive approach to cybersecurity is necessary in the current digital landscape, and these resources are an integral part of that strategy. Knowledge is power; mastering these tools will enable you to stay ahead of the ever-evolving threat landscape, granting your organization a crucial edge in security.
Keywords: #CyberSecurity #OSINT #SOC #SecurityAnalysis #ThreatDetection #IncidentResponse #DataBreach #VirusTotal #Shodan #HaveIBeenPwned #Censys #GoogleDorks #OSINTFramework #PublicWWW #AlienVaultOTX #WhoisLookup #Intelxio #ThreatIntelligence #InternetSafety #CyberDefence #InfoSec #DigitalSecurity #CyberThreats #OpenSourceIntelligence #DataSecurity #NetworkSecurity #IoTSecurity #MalwareDetection #DomainLookup #CyberRisk