Every week I read about another traveller that is hassled at the border to turn over his laptop, tablet or smartphone and their associated passwords. Knowing that a stranger has gone through your personal “stuff” feels dirty (similar to being robbed).
A question I get asked often by readers, friends and colleagues is “How do I travel through international borders without worrying that my life will be put on show for some stranger with a badge?”. You don’t believe that this can happen; here are some interesting articles:
TSA employee caught stealing cash from woman's luggage at security checkpoint
Canada Border Services seizes lawyer's phone, laptop for not sharing passwords
Operational Security 101
The work of physical security and digital (cyber) security are merging fast and you cannot have one without the other. So what is a traveler to do?
Identify your sensitive data. Before travelling, conduct an extensive analysis of the data you will be crossing the border with. This doesn’t just include intellectual property or employee information but remember that once authorities have access to your email, without you present, they can figure out what social media accounts you have, they can reset your password for any site, they can build a social graph of all your contacts (using your email, instant messages and contacts), etc.
Prepare a lists of vulnerabilities you are subject to? You should consider everything from device theft to authorities riffling through your personal data with no regard for privacy.
Determine your risk level for each vulnerability. As long as you back up your data and your device is encrypted, then your risk after a theft is limited to the cost of replacing your device or scrambling to buy a new one while in transit. You will realize your risk level quickly rises when you consider the exponentially increasing risk of having your device analyzed at the border.
Design your countermeasure plan. For each vulnerability, design a mitigation or risk minimization plan. This is what the rest of the article will talk about.
Countermeasures
Like a broken record, I will now extol the virtues of the Chromebooks and why many security professionals rely solely on these devices when security is essential. I know many of you will email me to explain why Google is evil and shouldn’t be trusted. I respect everyone’s opinion, and if you believe using Google products and services doesn’t meet your security requirements, then, by all means, choose something else.
A Chromebook is designed to be reinitialized anytime and to restore its state very quickly. Log into a device connected to a respectable network, and within minutes, you are back up and running with your apps, extensions, bookmarks and settings. Your data is stored in the cloud, and local device storage is encrypted.
Theft
If some numskull steals your device, you will have to buy a new one but at least your data is safely stored in the cloud, and there is no unencrypted data locally to expose you. I have had my device stolen on a train in Europe (on my way to speak at a conference). At my destination, I bought a Chromebook, used the store's WIFI to restore my device, and I was up and running within 30 minutes.
Border inspection
Border inspection is a different beast because they have the authority to force you to turn over your passwords. In this case, the only protection strategy is trickery.
For people crossing the border with sensitive information, I recommend that you use a Chromebook and sync everything to the cloud. Before travelling, you Powerwash the Chromebook (aka set it back to factory default) and then log into it with a dummy Google account.
This Google account should have some emails, contacts, favourites, files stored on your Google drive, etc. It should look like it is an authentic and genuine account. When your device is inspected, it will have nothing of interest, and you will not endanger your “real” data.
Once you cross the border, find a WIFI network, Powerwash your device and log in with your “real” account.
What about your smartphone
I trust the Chromebook Powerwash process enough to reuse a Chromebook that was inspected by border security but not a smartphone. Smartphones (iPhone or Android) do not have the excellent backup and recovery properties of the Chromebook. In most cases, I travel with a real fully loaded smartphone and will destroy it if it is ever taken from me. I will immediately change all my passwords and implement honeypot style detection tools to see if they attempt to exploit me.
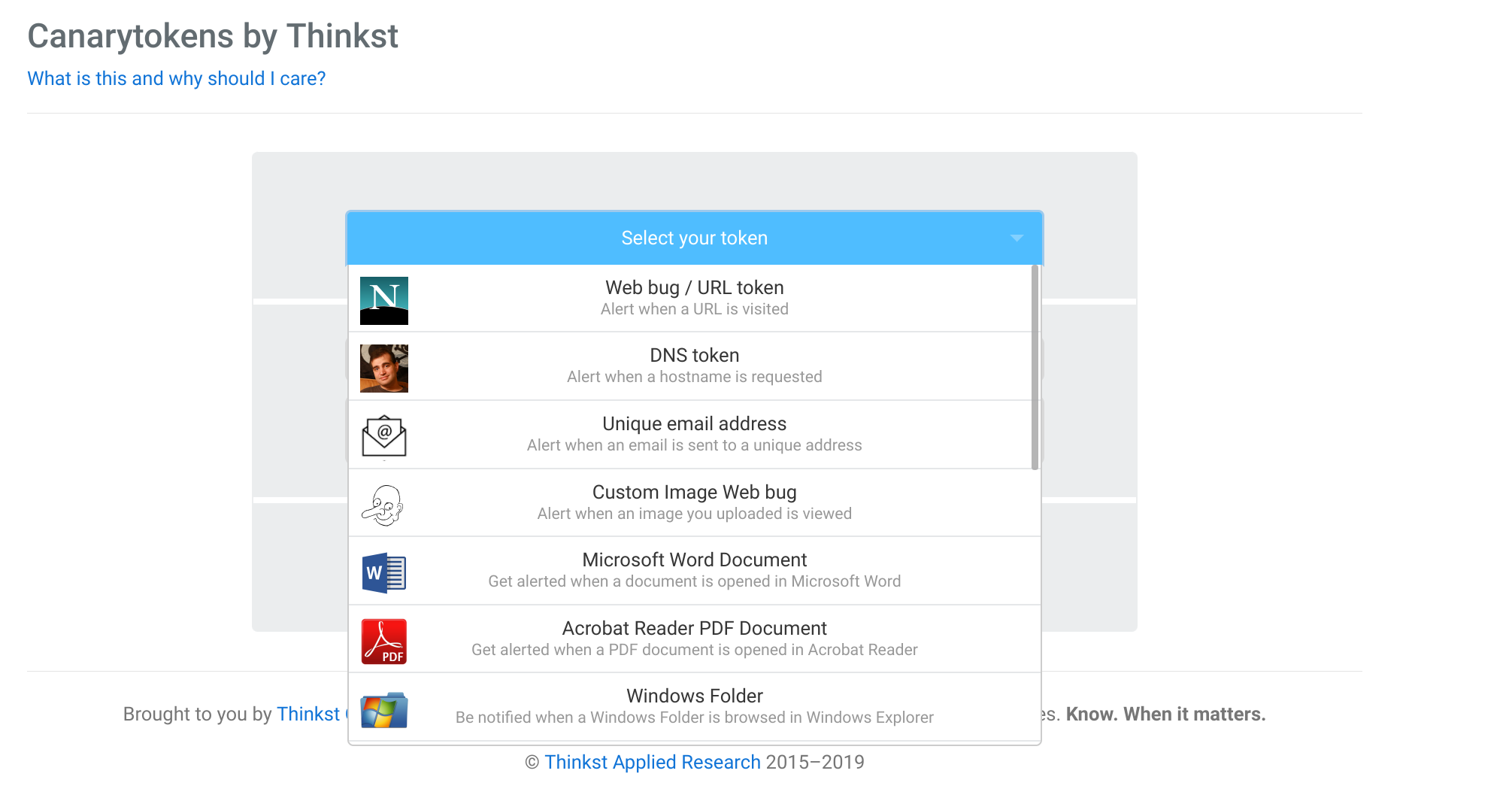
What are these detection techniques I am talking about? Well one example is to use the Free Canary Tokens to generate different honeypots in your work environment.
As an example, you create an easy to find (weaponized) Word or PDF file (stored in your Google drive) and phone that sends out a beacon when it is opened. Think of these tools as motion sensors warning you that your digital being is at risk and that you need to take extraordinary measures to protect yourself.
Conclusion
An article about traveller airport border crossing security (OPSEC) can be very long, but I wanted to give you a gentle introduction. If you are a journalist, politician or senior executive at risk, hire a good security consultant to guide you. The most expensive advice is free advice.
If you are a journalist with a reputable organization working on high-risk reporting and need security advice, I am always available to provide free guidance. I believe free and open journalism is a pillar of our modern democracy.