Other related articles
Today I bring you a link to the Arvin Club darknet (Tor) ransomeware showcase site
Arvin Club offers ransomware leaks and leaks from breached sites.
As an example, they even offer the Clubhouse scrape data leak
Strategy, Innovation, Leadership and Security

Other related articles
Today I bring you a link to the Arvin Club darknet (Tor) ransomeware showcase site
Arvin Club offers ransomware leaks and leaks from breached sites.
As an example, they even offer the Clubhouse scrape data leak


Not a week goes by without some data breach, leak, hack, attack or other significant cybersecurity failures that spills all over blogs and even national media.
Five years ago, only avant-garde companies invested in cybersecurity; today, it has become a must. Companies realize the importance of a solid cybersecurity plan built on the People, Process and Technology pillars. One topic rarely discussed by corporate executives or security leaders is the incredible (and growing) stress the current environment inflicts on CISOs.

Stress is a normal way of life for most executives, but CISOs feel an acute level. Nominet's report, in collaboration with Vanson Bourne, The CISO Stress Report - Life Inside the Perimeter: One yes on", was the first quantification of this systemic issue.
In 2019, Nominet and Vanson Bourne conducted 800 online interviews in the USA and U.K (400 C-Suite and 400 CISOs). The included CISOs worked for both public and private corporates with at least 3,000 employees. They were quizzed about work-related stress and its effect on their professional & personal lives.
88 percent of CISOs consider themselves under moderate or high levels of stress

7 out of 10 CISOs agree their work-life balance is too heavily weighted towards work (71%)
Almost all CISOs are working beyond their contracted hours, on average by 10 hours per week (95%)
This equates to extra time worth $30,319 per annum
87% of CISOs say that working additional hours was expected by their organization, while 78% of board members admitted this to be the case
83% of CISOs spend at least half of their evenings and weekends thinking about work
Only 2% say they are able to switch off once they’ve left the office
Over a third have failed to take all entitled annual leave
45% have missed family milestones or activities
The average tenure of a CISO is 26 months, and many believe stress is the primary motivator of change.
CISOs reported missing important family events such as birthdays, vacations, weddings and even funerals. Even with all the stress and extra working hours, most CISOs aren't taking their full annual leave (or sick days, time off for medical & dental appointments, etc.)
Stuart Reed, vice president at Nominet, suggested that the stress and wear & team on CISOs result from a combination of internal and external factors. The external factors are the headlines your read about, while the internal stresses are the pressure from executives expecting CISOs to "properly" handle these incidents and to provide updates & answers continually.

44% being responsible for securing the organization and preventing breaches
40% the need to stay ahead of threat intelligence
39% the long hours worked
65% of those surveyed had suffered a breach in the past 12 months
37% of CISOs consider themselves ultimately % responsible for a breach while 31% of board members agree
A fifth of CISOs believe they would be fired as a result, regardless of whether or not they themselves were responsible

Nearly half of CISOs said the levels of stress they are under has impacted their mental health (48%)
35% also reported that their stress had impacted their physical health
4 out of 10 CISOs said that their stress levels had affected relationships with their partners or children
31% said the stress affected their ability to fully perform at their job

A quarter of CISOs are turning to medication or alcohol to manage their stress - an increase from 17% a year ago
A fifth have taken a leave of absence due to stress (21%)
21% believed there to be no support structures in place within their organization to help deal with stress, while 94% of board members suggest there are
9 out of 10 CISOs would take a pay cut to improve their work-life balance; on average 7.76%, equating to $9,642

The report suggests that boards of directors are aware of the stress affecting their CISOs (74% of respondents believe that moderate or severe stress impacts their CISO).
As the board of directors and CIOs acknowledge this significant issue, they show more willingness to hire support staff to alleviate some of the stress elements. Ensuring the CISO is surrounded by skilled senior professionals can help alleviate many of the most aggravating elements. These supporting professionals must be experienced security technicians and have strong business acumen, strong interpersonal skills and the ability to work in teams or alone.
Another important stress reliever is ensuring the CISO can honestly share the state of their cyber universe with the executive leadership team to ensure decision-makers universally understand risks and provide executive support to the CISO (guidance and funding). The CISO must know he/she is not alone.
Cybersecurity is growing in importance and, for many organizations, has become the price of entry. Executives have started to understand this important fundamental truth and are now more willing to share the cybersecurity burden.
I built my first security business (a Canada wide security practice) that was later sold to Bell Canada in the early 2000’s and have been actively involved in cybersecurity since. Over the last 20+ years, I have seen the importance of security grow and this has required the creation of the CISO role.
Unfortunately I see too many CISOs that have been promoted to their level of incompetence (read about Peter’s principle here). The job is difficult enough for the professional with the right skills but is deadly for the wrong professional promoted as a reward (not because of merit).
Companies should perform an honest review of their CISOs competence and abilities. Thrusting the wrong person into this role is a disservice to the candidate.
Additionally it is important to realize that most security certifications tackle the technical skills. These are important but form less than 40% of the CISO’s true day to day responsibilities. The key skills (negotiation, strategic vision, budgeting, people management, etc) are completely ignored in most of the certifications companies deem “required” when posting a CISO job. HR leaders must quickly understand the new realities of the CISO role and craft job descriptions akin to that of a business executive leader than a manager for firewalls. This realization is important because a properly skilled CISO will handle the stress much better and therefore will deliver a much higher return on investment for the company.
HR leaders must learn to hire the right candidate for the CISO position

There are hundreds of write-ups about the CL0P Ransomware and the grand behind it. They came back into the spotlight recently claiming to have exploited the Accellion FTA (old file transfer service) and thus customers running unpatched version of the Accellion product.
Over the last couple of weeks, more “leaks” have come out claiming many more companies have been breached through this vulnerability and then infected with the Cl0p ransomware.
Many have asked if I knew where (on the Darknet, aka TOR network) the CL0P gang is publishing the list of infected companies. the answer is yes : http://ekbgzchl6x2ias37.onion/

Now a word of caution. We aren’t certain who created this site. We don’t know if data on the site is actual CL0P infected organizations or simply someone that found the leaks and is claiming they are infected.
My research leads me to believe that the CL0P group is behind this TOR site and that the data on it is indicative of infected organizations.
If you click on Canadian Bombardier, you get this page with some data provided as proof.

Here is a sample of the “proof” they provide for Bombardier

The moral of the story is that there are bad people our there that want to profit from the misery of others. These threat actors are getting more creative and have improved marketing skills trying to “encourage” victims to pay up.
Hire a good CISO and invest in your security program.

Security and usability are contradictory forces. Ultimate usability means less security and ultimate security mean less usability. It is a fine balancing act tat every user must perform themselves.
The iPhone is a well designed and fairly safe device out of the box but there are some settings you can change to reduce your odds of getting attacked. Each setting that you change will make your device a bit more secure but will limit a useful functionality.
This article will walk you through some of the settings that will reduce your susceptibility to software exploitation.
Your iPhone should be configured (out of the box) to periodically download software and OS patches but you should check manually every day (to ensure you get the patches as quickly as possible)..
Although the iPhone has a very mature and sophisticated security model (including sandboxing), we have seen advanced threat actors use zero-day attacks sold by vulnerability merchants to attack freedom fighters, journalists and other people of interest.
Like on a traditional computer:
never open an attachment from an unknown person
never open an unexpected attachment from a known contact
never click through on a link (SMS, Whatsapp, Telegram, Twitter, Facebook, Instagram, etc) from an unknown person
never click through on a link from a known contact but an unexpected message
We have seen many sophisticated and advanced attacks performed against iOS devices that leverage unknown (therefore unpatched) vulnerabilities but many of them are not persistent. This means that the attacker has to re-compromise your phone if they want control, after a reboot. Think of the reboot as a cleanse or detox.
This has become a standard ritual for me and I regularly restart my phone throughout the day.
Apple has implemented an ingenious feature to quickly show you if an app is using your camera or your microphone. When in use, an orange or green dot will appear on your top menu bar next to the battery indicator.

An orange indicator means the microphone is being used by an app on your iPhone. Remember that if you are legitimately using this for features like Siri, it is normal that this will show up but it should disappear when you are done or it means something is still listening in (legitimate or not).
A green indicator means either the camera or the camera and the microphone are being used
If you swipe Control Center open, on the top, it will show you the last app that triggered the microphone or the camera


Airdrop is an Apple technology that allows you to quickly and easily share content (files, videos, music, links, etc) between IOS and macOS devices. AirDrop itself could have vulnerabilities that could allow an attacker to send a malicious attack file to your device without your knowledge or they can perform social engineering attack to trick you to click on a malicious file.
Swipe up (on older phones) or down from the right-hand side of the screen (on modern devices) to show the control center
3d touch or long-press the network settings card (in the upper left-hand corner, then click on AirDrop)
Choose Receiving Off to disable AirDrop

Bluetooth has had many easily exploitable vulnerabilities in the past. Although Apple quickly patches vulnerabilities, there may be unknown vulnerabilities being sold by vulnerability merchants to threat actors or nation-state attackers. Additionally many organizations (from law enforcement to shopping mall managers) are known to track users with their Bluetooth ID.
If you are not actively using Bluetooth (aka connected to headphones for example) then you should consider disabling it. Disabling it will cut off the connection between your phone and Apple Watch (until you turn it on again).
Swipe up (on older phones) or down from the right-hand side of the screen (on modern devices) to show the control center
Click on the Bluetooth icon to turn it off

JavaScript powers the modern web but has been used in a significant number of web attacks. Disabling JavaScript will significantly improve the security of your device but will likely break many modern websites (rendering them unusable).
If you are a higher-risk individual (politician, journalist, dissent, etc, then you may want to turn JavaScript off. Otherwise, you may want to ignore this change (aka leave it on). Changing this setting only applies to JavaScript inside of the Apple Safari web browser.
Open the Settings App
Find Safari
Scroll to the bottom until you see Advanced
Turn of JavaScript by tapping the toggle switch.
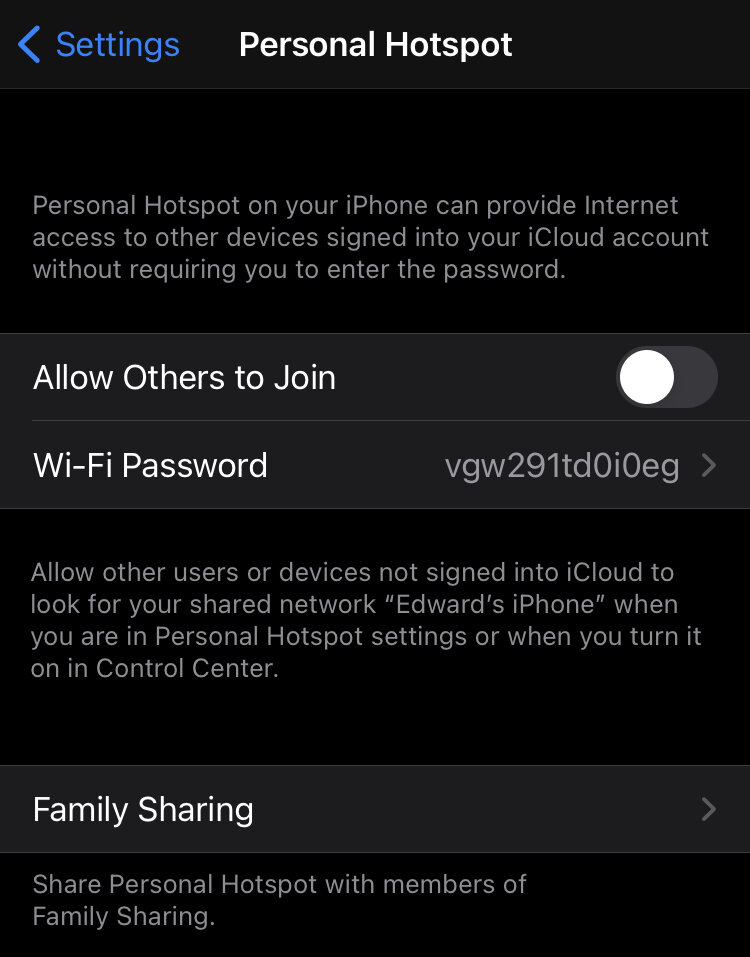
The WIFI Hotspot is a setting that is normally set to off. I am specifying it here in case you turned it on.
WIFI hotspot allows other WIFI devices to connect to your smartphone and share its LTE connection (3G, 4G or 5G). Obviously, those devices need to have the WIFI Hotspot password that is configured on your smartphone, but it is possible iOS contains a vulnerability not yet known by Apple that could be exploited, this allowing a threat actor to connect to your device and push malware.
Open the Settings App
Open Personal Hotspot
Turn off Allow Others to Join

This is not a sponsored post and the links are not affiliate links. The links are provided to simplify your journey.
I wrote this post to help the average consumer user.
Many believe bad things only happen to other people, but the quantity and severity of breaches are growing quickly. Once you have accepted that you may be part of the unlucky, how do you know if your information was leaked in a breach?
First check HaveIBeenPwnd
Security researcher Troy Hunt has created this free resource to check if your email address was part of any known breach.
You simply enter the email address you used to register for most sites and it will give you a green sign (you are not in any data breach) or a red sign (your email was found in a data breach):

HIBP does not store any emails you use to search for breaches, unless you sign up for their automatic notification service. By listing the sites that leaked your credentials, you can determine what other sites may now be at risk (because the majority of you reuse passwords).
Second, you may want to checkout another similar service operated by the non-profit Mozilla foundation called Firefox monitor.

this works the same way as HIBP. You enter your mail and press check. Similar to HIBP, if your email address was in a known leak, they will list the sites (or breaches):
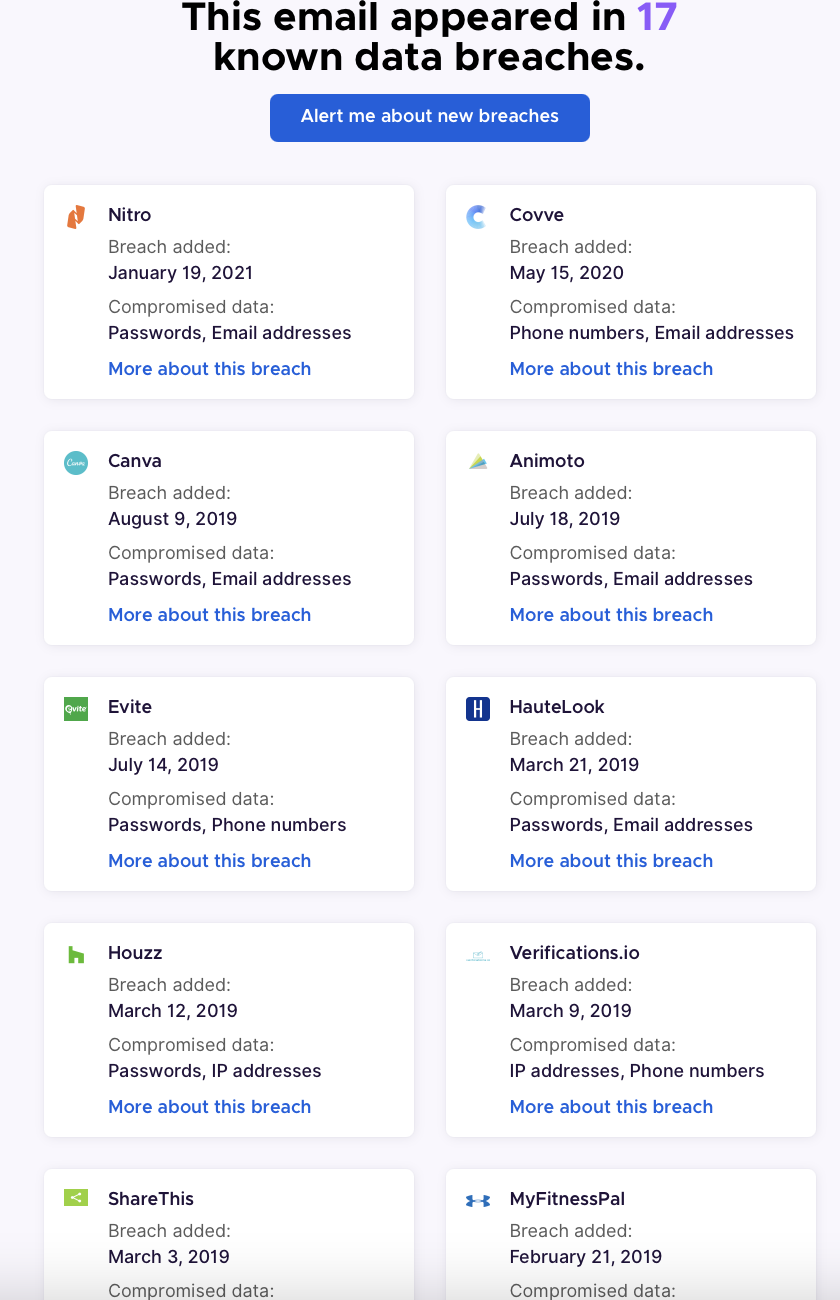
The third source you can check is a site called cybernews

Like HIBP and Firefox Monitor, you enter your email address and the site returns a list of breaches your information was found in:

Unlike the others, this one does not provide a list of the breaches (or number) your information was found in. This could be a good third check.
I recommend checking these sites monthly or using their auto-alert feature, which will email you if your information is found in a future breach.
BIG IMPORTANT WARNING:
If these sites do not find your information in a known breach, it does not mean you are safe. There are probably hundreds or thousands of breaches that occur each year that go unannounced and therefore these sites cannot catalog that information. Always be careful and we will provide some extra insight later in this article.
As mentioned above, not being included doesn’t mean you are safe. So always be vigilant with your online accounts. Sites or services with good security controls will detect anomalous activity related to your account and will email you. As an example, if you receive a password reset link, that you didn’t request,
Or if a site emails Askin if you have logged in from a location you didn’t log in from (you log in from the USA but the email says someone from Prague attempted to log into your account). Gmail does this (for unusual browsers, IP addresses or geographic locations).
Sometimes when accounts are taken over, the attacker will change the registered account email so if you try to log into a service you are registered for and it does not recognize your email address, that is an indication your account was taken over.
Another indicator is strange configurations in your email accounts. Attackers want to get into your email because that is how they can reset service account passwords or delete alerts so you are not tipped off they are trying to break into your account. They can either set up filters in your email (to forward emails of interest to them or mark alert warning emails as read and immediately delete them) or they can set up forwarding of your emails to another email address they control.
The main issue is password reuse. Most users have a handful of passwords they reuse for all the sites they register on. Once an attackers finds that password, they will try logging into other major services (Facebook, twitter, Instagram, Gmail, Hotmail, etc) and will have immediate access.
This is why I recommend using long unique passwords for each site and storing those passwords in a reputable password manager.
My favourite password managers (free and paid)
five sites to help you generate long, complicated and unique passwords
With the quantity and size of breaches, it is likely that your information was leaked in a breach, what do you do now?
If you reuse passwords, then the first thing you should do is visit all the sites you use and immediately change the passwords.
If you are locked out of your account (if could mean the attackers have done an account takeover), use the reset password functionality to change your password.
If you are sure you had a registered account but the system can not find your email address (when you use the above reset feature), it could mean the attackers have changed the registered email address for your account. You will have to contact the support team for the site in question and explain the situation.
Another interesting recommendation you don’t see often is to use multiple email addresses. If you are using a password manager (and you should be by now), then why not create a free email address for different groups of services. Maybe one for online shopping, one for social media, etc
Use long, complicated and random passwords for each site. Something like f%[_8s9f579o+*38zjURqjK}GQZ
You can also use long passphrase (if you are stubborn and don’t want to use a password manager) but make it unique for each service: 1l0v3*K1nG!*Appl3?P3acH%Umrellas-P1nk!
Most sites use a technique called hashing to store user passwords. This means that they don’t store your password but a mathematically derived result and hackers have to “crack” the hashes to reverse them back to passwords. This cracking function is done with trial and error and is impractical for long and complex passwords. So even if your data is leaked in a breach, they may not be able to reverse the hash and your account may end up being “safe” if you use long and complex passwords.
Never reused a password for multiple sites.
whenever possible, use two factor authentication to add additional security to your account.
There is a great free site called twofactorauth that has an exhaustive list of sites that allow users to leverage 2 factor authentication and even provide a link to the info page on how to turn it on for many of those sites

The most secure is using a hardware token (my favourite token is the Yubikey ones) and the least secure is SMS. If you are curious why SMS isn’t secure, I wrote an old article about the SS7 attack.
If you choose to use a software token, the one I recommend is Authy by Twilio Authy is free, cross-platform and incorporates good security protection features.