VPN Unlimited is one of the most popular VPN services available and for good reason. It is fast, reliable and competitively priced (deal below).
VPN Unlimited is a USA based provider and offers termination in more than 30 countries (with multiple locations in most countries). VPN Unlimited has good platform support (Windows, Mac, iPhone, iPad, Android) and very well written clients.
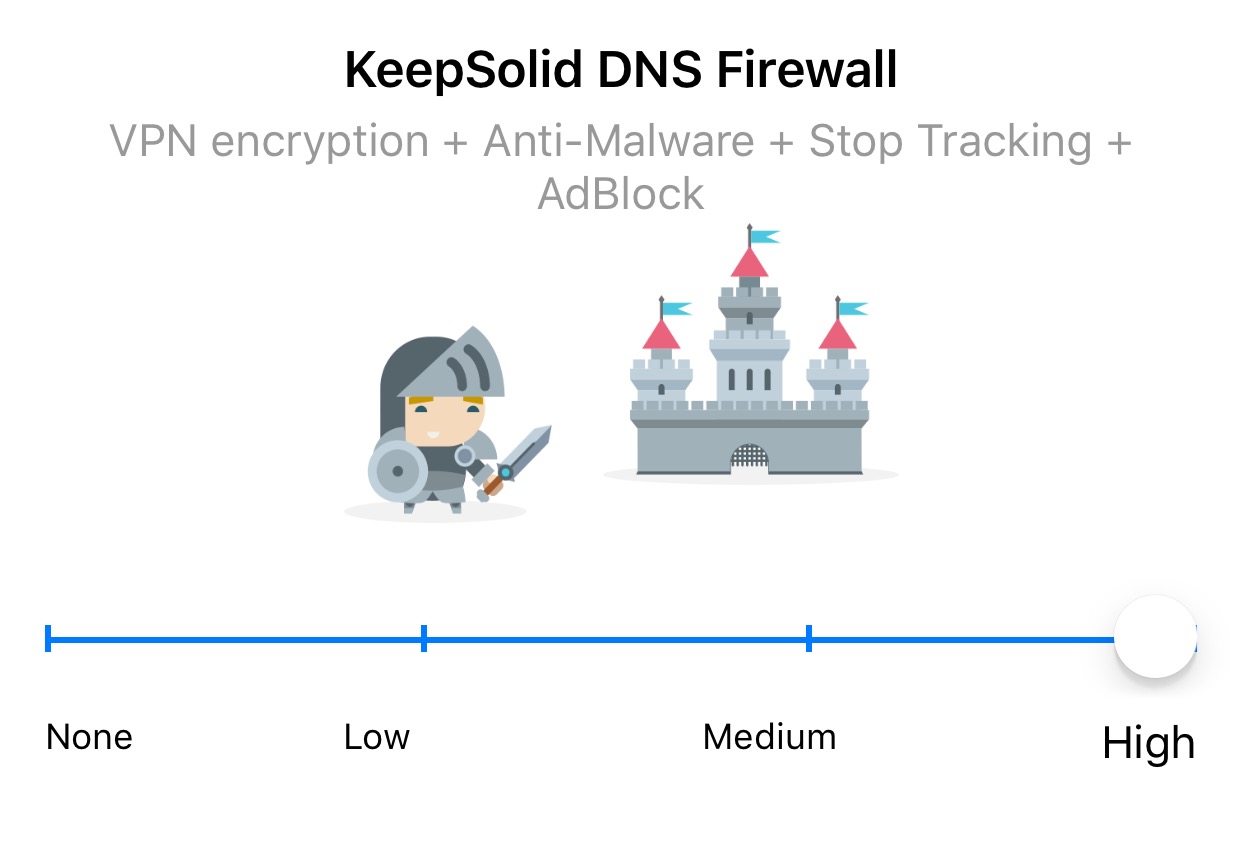
Above is a screenshot of the protection menu option on their IOS client. When set to High security, they (in addition to VPN protection) automatically add anti-malware, tracking blocking and ad blocking.) All of this extra security is done at the network layer without the need to configure any additional applications or pay additional fees.
Like most VPN service providers, VPN Unlimited specifically mentions that they do not allow illegal torrenting via their service. They recognise that not all torrents are illegal and allow the use of the BitTorrent protocol on these VPN termination points: US-California 1, Canada-Ontario, Romania, Luxembourg, and France servers.
A question I get asked often is "Does VPN Unlimited support OpenVPN on iOS, iPhone or iPad?" The answer is Yes! As shown in the above screenshot. Additionally, they support a protocol they call KeepSolid Wise (similar to the Chameleon protocol on VyprVPN). KeepSolid Wise uses common ports (TCP 443/USP 33434) which help bypass firewall restrictions and packet shaping control for most environments. KeepSolid Wise is available on iOS, Android, MacOS, Linux and Windows clients.
I setup VPN Unlimited on a Windows machine configured for maximum privacy. I then ran a battery of tests to determine how well it protected my privacy.
- does not leak DNS queries when in VPN mode (go here to test)
- does hide your actual IP address (go here to test)
- does not leak IP or DNS information via JAVA or Flash ( Go here to test)
- protecting P2P traffic. Although I do not condone or encourage the use of P2P tools to steal protected media, there are dozens of legitimate uses for P2P technology. It is important to ensure your VPN product protects you while using P2P and VyprVPN did. You go to this site and the find the Torrent Address Detection. You download their magnet link into your P2P client of choice then activate the test. If it shows your real IP or DNS, you are not protected. You should only see your VPN address here.
- VPN Unlimited is not subject to WebRTC leaks when in VPN mode (go here to test
VPN Unlimited seems well written and does offer good protection.
Deal
VPN Unlimited is currently running a couple of specials that are worth considering (I bought the unlimited plan):
- KeepSolid VPN Unlimited lifetime subscription for only $49.99 (for 5 devices)
- KeepSolid VPN Unlimited 3-year subscription for only $29.99 (for 5 devices)
- Add their Infinity Plan (aka 5 additional device licenses) for $14.99 but you must own one of the above subscriptions
Conclusion
The best summary I can give you is that VPN Unlimited has a permanent stop on the first page of my iPhone and I use it regularly.
VPN Unlimited has decent privacy policies but isn't the super secret spy-proof identity protection service. If you want to protect your connection while out and about, VPN Unlimited is cheap, fast and reliable. If you want a super secret identity protecting connection then create your own VPN service on AWS or Azure using one of the pre-made scripts.
Questions
Does KeepSolid Wise work in China?
China severely controls encryption and in some cases slows down encrypted connections making them barely usable. A friend recently travelled to mainland China and reported that VPN Unlimited (with KeepSolid Wise UDP) worked flawlessly.
Does KeepSolid VPN Unlimited support video streaming?
Some of the cheaper VPN providers limit the quality of video from streaming sites because these stress the technical infrastructure of the provider. VPN Unlimited supports streaming video on all termination points but also makes available streaming optimized termination points which are specifically designed to work "better" with sites like Youtube, Dailymotion, Vimeo and more.
Does KeepSolid VPN limit connection speed?
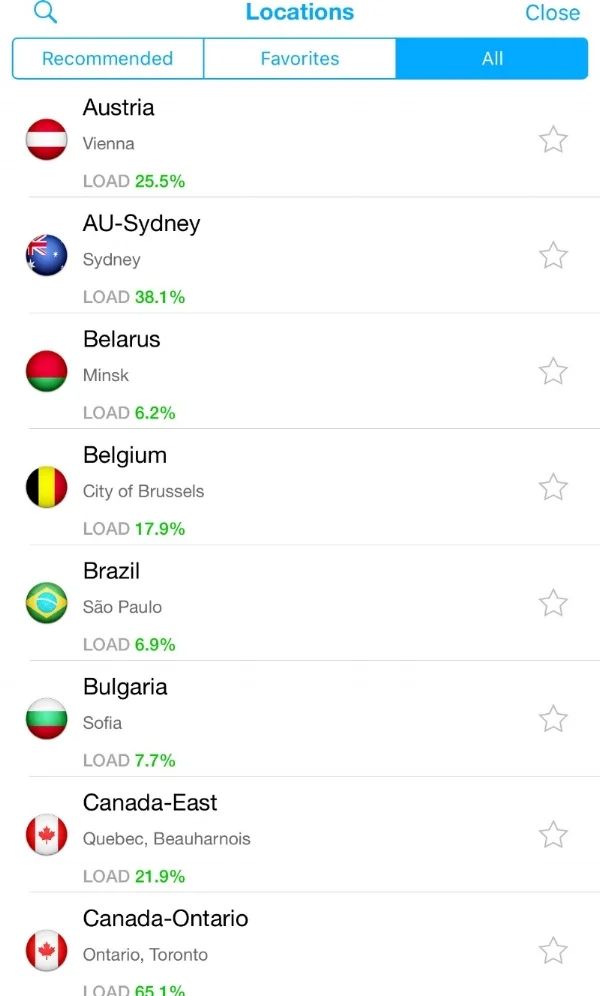
There are dozens of factors that contribute to your overall internet speed but VPN Unlimited does not have tiered pricing based on speed and does not limit connection speed in any way. On most clients, they even show the workload on each termination point which means you can choose one with the least amount of current load (which should lead to better performance).
Does VPN Unlimited support Chromebooks?
VPN Unlimited has a Google Chrome plugin (which works on Chromebooks) and allows you to protect your web browsing only. Obviously as a proxy, it is less secure and missing many of the additional features you expect from VPN Unlimited but it is a great way to browse quickly (securely) and a great option on a Chromebook that doesn't require Jedi level knowledge to implement.