Amazon Prime Day is here and expect millions of customers to go crazy buying things they don't need. At least those unneeded items are deeply discounted, right? Maybe! Thousands of items will be sold at their lowest price ever, but that isn't the case for everything.
The internet is here to save the day again. A free online tool called CamelCamelCamel will show you the truth.
You paste an Amazon link into the search bar at CamelCamelCamel and it will show you the item's price over time.
You copy the Amazon URL into the CamelCamelCamel search bar
Then you scroll midway down the results page and notice that the current promo is actually a good deal.
CamelCamelCamel covers Amazon sites for Canada, USA, Australia, China, France, Germany, Italy, Japan, Spain and the United Kingdom.
Do you want an example of a not so good deal? Here is one for you:
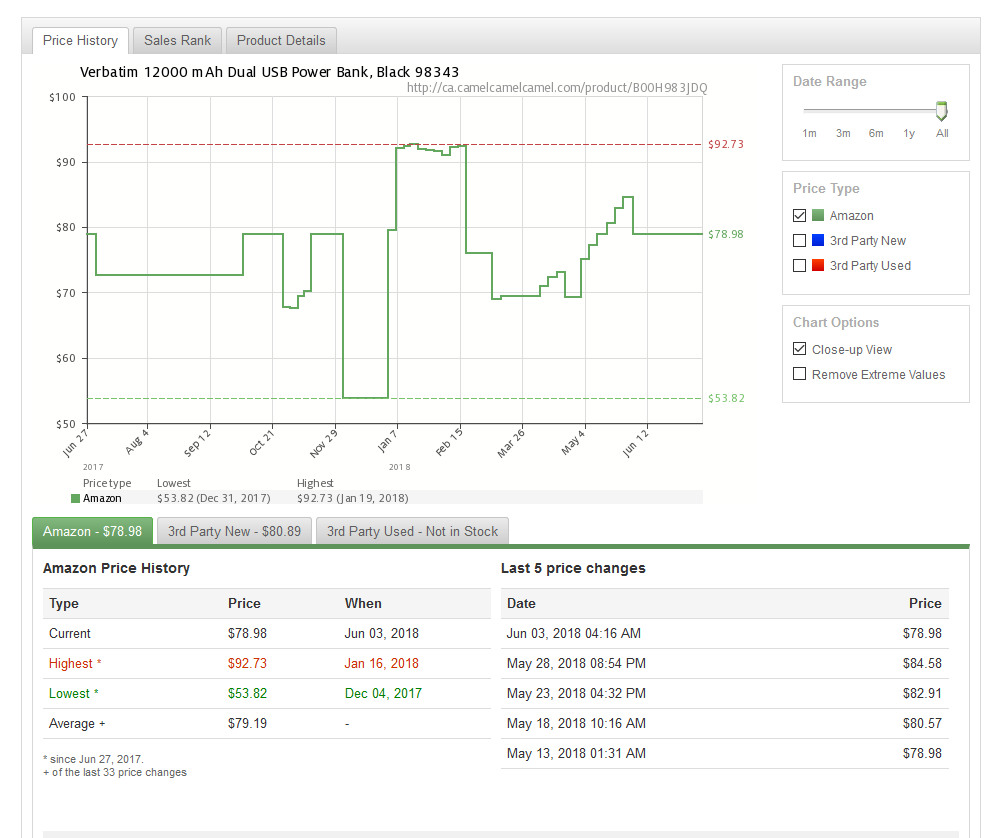
Looks like a good lightning deal...
CamelCamelCamel says this item was sold December 2017 for $53.82, a full $6.48 cheaper. This means that if you don't need this item right away, you may want to wait a bit or find an alternative that may actually be a deal.
And one more thing
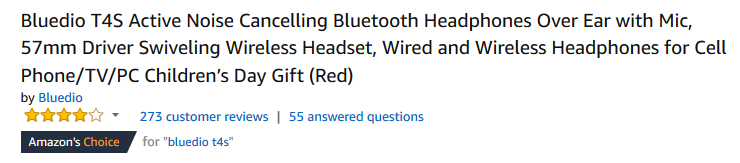
I'll sweeten the pot with one more tip for Amazon Prime Day (PrimeDay) and this one is related to the product reviews. You will notice that those Bluedio headphones seem to have a good user review rating of 4/5 stars (with 273 customer reviews). Can you trust those reviews?
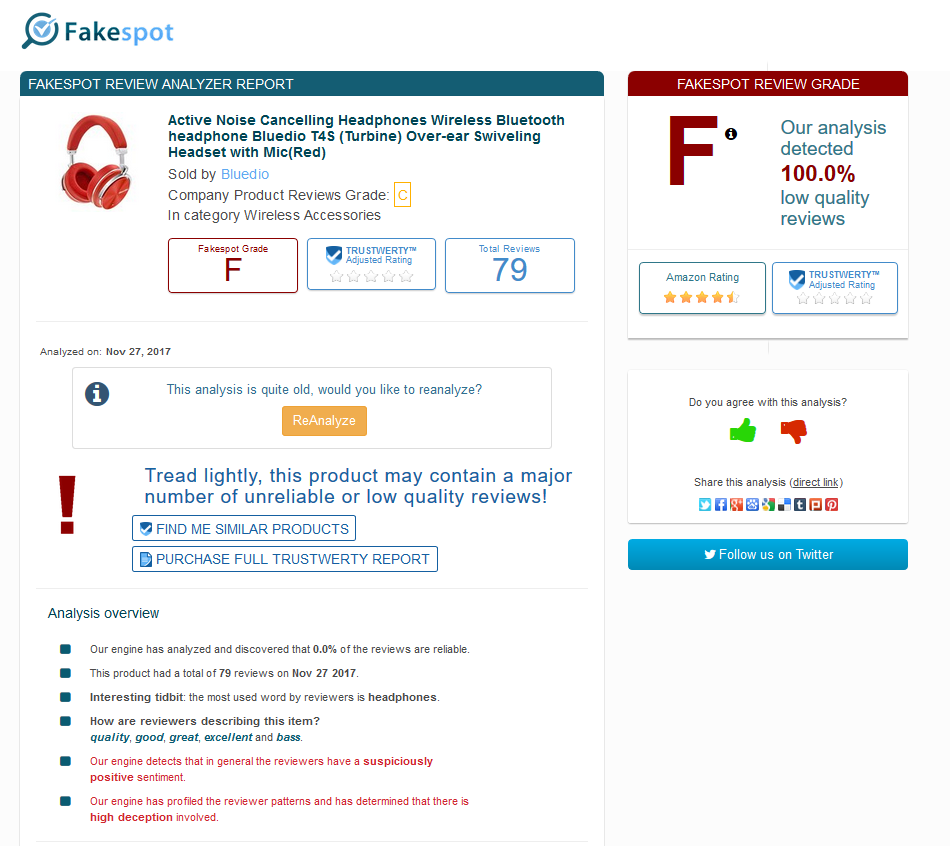
Enter Fakespot! Like CamelCamelCamel you copy the Amazon product URL into the Fakespot search bar and you are presented with a review reliability score
Fakespot isn't perfect but it is a great way to quickly determine how much trust you should put in the user reviews. Notice above the analysis is old. if you see that button, press the ReAnalyze button and wait until you get a new rating.
When I tested Fakespot with these on-special headphones, the user review rating improved from an F to a D.
The moral of the story is that you will probably find hundreds of great deals worth the asking price but make sure to perform your own due diligence using CamelCamelCamel and Fakespot.